Government of Canada Cloud Security Risk Management Approach and Procedures
Foreword
Cloud computing has the potential to deliver agile and flexible information system services. Under the cloud computing paradigm, the Government of Canada (GC) relinquishes direct control over many aspects of security and privacy, and in doing so, confers a level of trust onto the cloud service provider (CSP). At the same time, GC departments and agencies using cloud services remain accountable for the confidentiality, integrity, and availability of the GC information system and related information hosted by the CSP.
As a result, GC departments and agencies must extend their information system security risk management practice to include cloud environments; however, the shared nature of operating and using a cloud environment changes who is responsible for the implementation, operation, and maintenance of security controls. GC departments and agencies therefore need to understand cloud security and ensure risks are effectively addressed.
To enable the adoption of cloud computing, an integrated risk management approach and procedures have been developed to establish cloud-based GC services. These instruments are adaptations of existing risk management and cloud security standards from the US National Institute of Standards and Technology (NIST) and risk management guidance from the Communications Security Establishment (CSE).
Executive Summary
Cloud computing has introduced a fundamental shift in the way information system services are delivered and the Government of Canada (GC) has established a strategy Footnote 1 that will position itself to leverage this alternative service delivery model. Cloud adoption will ensure that the GC can continue to sustain service excellence during a period of increased demand by Canadians for online services and timely access to information.
This document describes the security risk management approach for the adoption of cloud-based GC services. It consists of the following activities:
- Perform security categorization (in terms of confidentiality, integrity, and availability) of each GC service being deployed on a cloud service;
- Select an appropriate set of security controls based on the GC service’s security category;
- Select the right cloud deployment model and cloud service model for the GC service;
- Assess the implementation of the security controls in the supporting cloud service;
- Implement the required security controls in the GC service;
- Assess the implementation of the security controls in the GC service;
- Authorize operations of the resulting cloud-based GC service;
- Continuously monitor the security of the cloud-based GC service during the operation phase; and
- Maintain the authorization state of the cloud-based GC service.
This approach and supporting procedures help to ensure that cloud service providers (CSPs) understand the GC’s security requirements, and that GC departments and agencies (or GC consumer organizations), and CSPs understand their shared responsibility in implementing the security controls with the appropriate rigour to allow the hosting of GC services and related information in various cloud environments.
On this page
List of Abbreviations and Acronyms
| CIRT | Computer Incident Response Team |
| CONOPS | Concept of Operations |
| CSE | Communications Security Establishment |
| CS EMP | Cyber Security Event Management Plan |
| CSP | Cloud Service Provider |
| FedRAMP | Federal Risk and Authorization Management Program |
| GC | Government of Canada |
| GSRM | Government of Canada Strategic Reference Model |
| IaaS | Infrastructure as a Service |
| IPC | Information Protection Centre |
| IT | Information Technology |
| ITSG | Information Technology Security Guidance |
| LAN | Local Area Network |
| NIST | National Institute of Standard and Technology |
| PAA | Program Alignment Architecture |
| PaaS | Platform as a Service |
| PBMM | Protected B, Medium Integrity, Medium Availability |
| PIA | Privacy Impact Assessment |
| PoAM | Plan of Actions and Milestones |
| RACI | Responsible, Accountable, Consulted, Informed |
| SaaS | Software as a Service |
| SDLC | System Development Lifecycle |
| SLA | Service Level Agreement |
| SSC | Shared Services Canada |
| TBS | Treasury Board of Canada Secretariat |
| ULL | Unclassified, Low Integrity, Low Availability |
1. Introduction
-
In this section
1.1 Background
Cloud computing has introduced a fundamental shift in the way information system services are delivered and the Government of Canada (GC) will position itself to leverage this alternative service delivery model. Cloud adoption will ensure that the GC can continue to sustain service excellence during a period of increased demand by Canadians for online services and timely access to accurate information. This developing shift will affect how we procure, secure, and work with information systems that support GC and departmental programs and services.
Under the cloud computing paradigm, the GC will depend on vendors for many aspects of security and privacy, and in doing so, will confer a level of trust onto the cloud service provider (CSP). To establish this trust, the GC requires an information system security risk management approach and procedures that are adapted to cloud computing.
1.2 Document Purpose and Scope
This document describes the authorities, approach, and procedures for managing security risks to GC services when they are hosted on cloud services provided by commercial service providers.
1.3 Audience
This document is to be used by business owners, project managers, system and system security practitioners, CSPs, and other vendors providing outsourced services as an initial source of guidance to ensure appropriate security risk management activities are completed when implementing cloud-based GC services.
2. Context
This section summarizes the context for the GC cloud security risk management approach and procedures.
2.1 Government of Canada Cloud Adoption Strategy
The GC cloud adoption strategy Footnote 1 will guide departments and agencies with the adoption of cloud computing services in a cost effective and secure manner. Departments and agencies will choose cloud computing services from several options that will include extensions to existing legacy solutions and private and public cloud offerings. The strategy supports two broad goals:
- Help bring balance to the supply of information system services with the demand for those services, and
- Provide a consistent approach to how risks of cloud adoption will be managed.
While the strategy empowers the GC in its adoption of cloud services, GC departments and agencies remain accountable for the confidentiality, integrity, and availability of GC services when implementing on or migrating to a cloud environment. GC departments and agencies will therefore need to understand cloud security and ensure that risks are effectively addressed.
2.2 Foundation Frameworks
The GC cloud security risk management approach and procedures were derived from the following cloud computing and information system security risk management standards, recommendations, and guidance:
- The Communications Security Establishment (CSE) information system security risk management guidance, which is published in Information Technology Security Guidance Publication 33 (ITSG-33) Footnote 2;
- The National Institute of Standards and Technology (NIST) standards on information system security risk management, which are specified in the 800 series of special publicationsFootnote 3 Footnote 4;
- The NIST cloud computing reference architecture, which is documented in Special Publication 500-292 Footnote 5;
- The NIST cloud computing security reference architecture, which is documented in Special Publication 500-299; and Footnote 6
- The Federal Risk and Authorization Management Program (FedRAMP), which supports the US government’s cloud first initiativeFootnote 7
2.3 Cloud Service Models
The NIST Cloud Computing Reference Architecture (Special Publication 500-292) Footnote 5 outlines the definitions of the various types of service models. Service models describe, broadly, what type of service the CSP provides to consumers: an application, a programming platform, or raw computing resources. In cloud computing scenarios, the cloud consumer has three different service models to choose from: infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS).
In an IaaS deployment, the capability provided to the consumer is to provision processing, storage, networks, and other fundamental computing resources where the consumer can deploy and run arbitrary software, which can include operating systems and applications.
In a PaaS deployment, the capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or acquired applications created using programming, libraries, services, and tools supported by the provider.
In a SaaS deployment, the capability provided to the consumer is to use the provider’s applications running on a cloud infrastructure. The applications are accessible from various client devices through either a thin client interface, such as a web browser (e.g. web-based email), or a program interface.
2.4 Cloud Deployment Models
Deployment models describe the relationship between the cloud service provider and cloud service consumer(s) – for example, the consumer may be one of many entities using a provider’s cloud service, it may have sole access to a particular service, or it may own and operate its own cloud. There are four cloud deployment models identified by NIST Footnote 5: public, private, community, and hybrid.
In a public cloud, the cloud infrastructure is provisioned for open use by the general public. It may be owned, managed, and operated by a business, academic, or government organization, or some combination of them. It exists on the premises of the cloud provider.
In a private cloud, the cloud infrastructure is provisioned for exclusive use by a single organization comprising multiple consumers (e.g. business units). It may be owned, managed, and operated by the organization, a third party, or some combination of them, and it may exist on or off premises.
In a community cloud, the cloud infrastructure is provisioned for exclusive use by a specific community of consumers from organizations that have shared concerns (e.g. mission, security requirements, policy, and compliance considerations). It may be owned, managed, and operated by one or more of the organizations in the community, a third party, or some combination of them, and it may exist on or off premises.
In a hybrid cloud, the cloud infrastructure is a composite of two or more distinct cloud infrastructures (private, community, or public) that remain unique entities, but are bound together by standardized or proprietary technology that enables data and application portability.
2.5 Actors
To be successful, the GC cloud security risk management approach relies on the activities of several actors, some operating independently of the GC. These actors are as follows:
- Cloud service provider (CSP): Any commercial provider of cloud services that wishes to offer its services to the GC. A CSP may or may not hold a certificationFootnote 16 for its cloud services when first engaging in the GC risk management process.
- Cloud service broker: An organization that acts as an intermediary between CSPs and consumers by providing various types of brokerage services including cloud marketplace.
- GC consumer organization: Any GC department or agency that wishes to acquire a cloud service to implement a cloud-based GC service.
- Third party security assessor: Any organization operating independently of CSPs and the GC that conducts security assessments under one or more security certification programs.
- GC security assessor: A GC organization (or individual acting on behalf of) that conducts security assessments of cloud services.
- Departmental security assessor: A departmental organization (or individual acting on behalf of) that conducts security assessments of cloud-based GC services.
- Authorizer: The GC organization accountable for the security of a cloud-based GC service and that must authorize its operations based on the results of security assessments.
2.6 GC Cloud Broker and Marketplace
Shared Services Canada (SSC) will act as the cloud broker for the GC. As such, SSC will be responsible for adding authorized cloud services from commercial CSPs to a cloud marketplace for selection and consumption by GC consumer organizations. SSC will also be responsible for other typical cloud broker responsibilities, including the management of relationships with CSPs, billing, and monitoring consumption of cloud services.
3. GC Cloud Security Risk Management Approach
This section describes the GC cloud security risk management approach to implement the GC cloud adoption strategy.
3.1 Process Overview
GC departments and agencies are ultimately responsible and accountable for the security risks incurred by their use of information system services offered by external suppliers, including the cloud services provided by CSPs and cloud brokers. As a result, the GC needs to adopt a structured approach for managing risks that accounts for the incorporation of cloud services into their information system services to support their program objectives and outcomes.
As shown in Figure 3-1, the GC cloud security risk management process consists of a series of procedures that are implemented by a combination of CSP and GC resources, except for authorization, as this procedure remains an inherent governmental responsibility that is directly linked to the management of information system security risks.
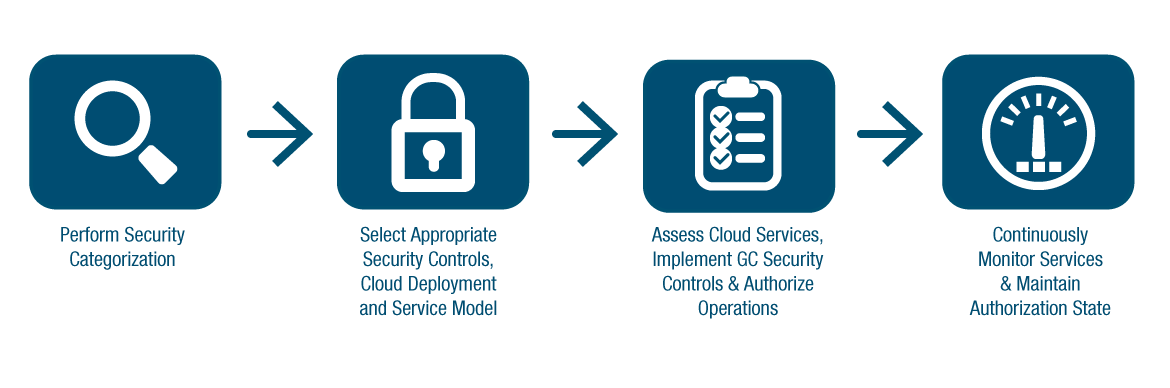
Figure 3-1 - Text version
The GC cloud security risk management process consists of a series of activities:
- Perform security categorization
- Select an appropriate set of security controls, cloud deployment cloud service model
- Assess the cloud services, implement the GC security controls, and authorize operations
- Continuously monitor services and maintain the authorization state
3.2 Security Categorization
Security category
A security category characterizes a business activity by the severity of expected injuries (injury level) from compromise with respect to the security objectives of confidentiality, integrity, and availability.
Security categorization is a fundamental activity of the GC cloud security risk management approach as it provides the basis for selecting an appropriate security control profile for cloud-based GC services. Through this process, the business activities that will be supported by a cloud-based GC service are identified and categorized, and the GC service inherits the resulting security category. The security category is then used to select a suitable profile.
Business activities are categorized by first determining the expected injuries from information system-related threat compromise to the national and non-national interests that the business activities serve, and then determining the level of these expected injuries.
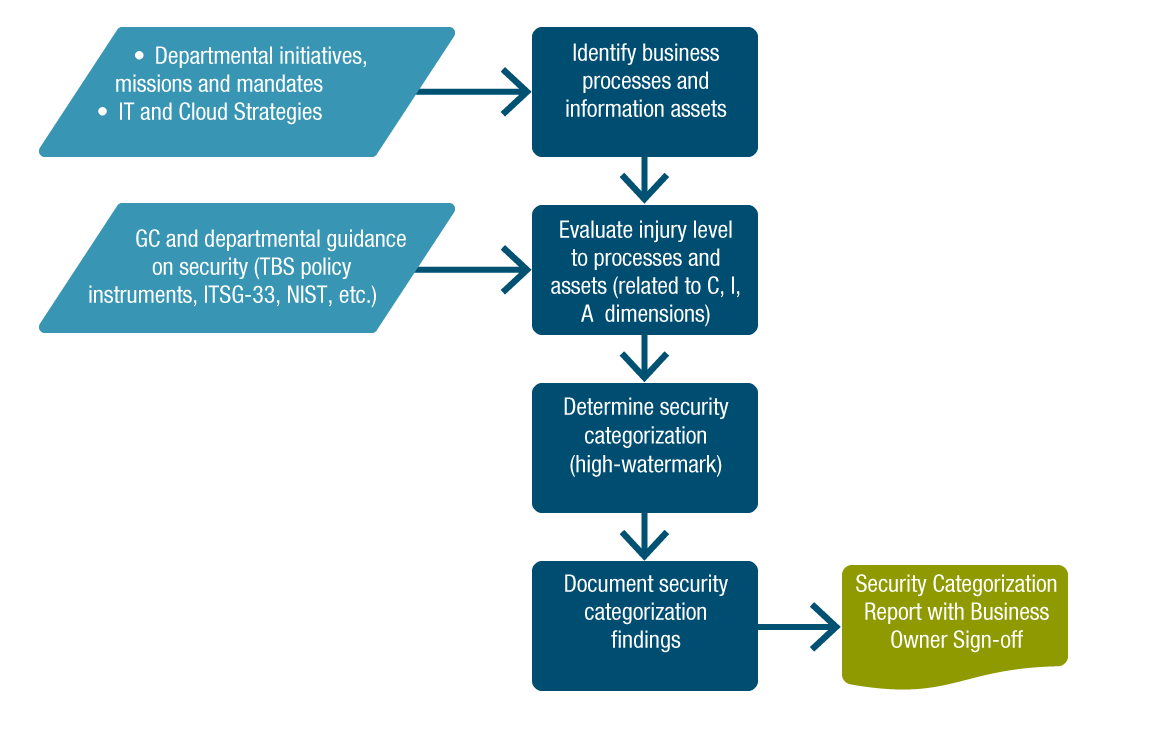
Figure 3-2 - Text version
The GC cloud security risk management process consists of a series of activities:
- Identify business processes and information assets with inputs departmental initiatives, missions and mandates, and IT and cloud strategies
- Evaluate injury level to processes and assets (related to Confidentiality, Integrity, and Availability dimensions) with inputs from GC and departmental guidance on security such as TBS policy instruments, ITSG-33, NIST, etc.)
- Determine the security categorization including high-watermark
- Document security categorization findings in a security categorization report that is signed off by the business owner
3.2.1 Concept of High Watermark
A business activity may be composed of business processes and information assets with differing levels of assessed injury. For example, one type of related information may have an assessed injury level of low and another type of related information an assessed injury level of medium for the same security objective. Similarly, a GC service may support several business activities, each composed of business processes and information assets having different injury levels. These individual values are important and should be documented. However, for the purpose of selecting the most appropriate cloud security control profile, the security category of the GC service should reflect the highest level of injury of all related business processes and information assets.
Determining the security category of a GC service therefore requires the business owner to consider the security categories of all related business processes and information assets. For a given GC service, the potential injury level values assigned to the respective security objectives (confidentiality, integrity, availability) must be the highest values (i.e., high water mark) from among those security categories that have been determined for each of the business processes and information assets.
For example, a department may decide to implement an information system service to support two business activities, one having an overall security category of (Protected A, Medium Integrity, Medium Availability), and another having an overall security category of (Protected B, Medium Integrity, Low Availability). In this case, as illustrated in Table 3-1, the information system service would be attributed the security category of (Protected B, Medium Integrity, Medium Availability).
| Business Activities to be Supported by GC Service | Security Category | ||
|---|---|---|---|
| Confidentiality | Integrity | Availability | |
| Business activity 1 | Protected A | Medium | Medium |
| Business activity 2 | Protected B | Medium | Low |
| GC Service | Protected B | Medium | Medium |
3.3 Security Control Profile Selection
Security control profile
A security control profile specifies for implementation a set of security controls to protect information systems supporting specific business activities when operating in specific technical and threat contexts by following specific security approaches.
As part of the GC cloud adoption strategy Footnote 1, security control profiles have been developed for cloud-based GC servicesFootnote 8. These profiles are derived from generic profiles developed by CSE (Annex 4 of the CSE ITSG-33 Footnote 2) and NIST (Special Publication 800-53 Footnote 9).
The GC cloud profiles:
- Represent the baseline security controls required to be implemented by CSPs and GC consumer organizations at selected security categorization levels;
- Incorporate a number of Canadian-specific security controls (called for by Canadian legislation or policy instruments) which are described in the CSE ITSG-33 catalogue; and
- Specify which security controls fall under the responsibility of the CSPs to implement and operate.
When implementing a cloud-based GC service, GC consumer organizations need to select an appropriate GC cloud security control profile. Once selected, a GC cloud profile serves as the basis to implement and assess security controls in cloud-based GC services.
3.4 Cloud Deployment and Service Model Selection
As described in Section 2, cloud-based information system services operate under different deployment models (public, private, community, and hybrid) and service models (IaaS, PaaS, and SaaS). When deploying to a cloud service, GC consumer organizations need to determine the type of cloud deployment and cloud service for their GC service. This selection will be motivated by several factors, for example, the nature of the GC service, how much control the GC consumer organization wishes to have over the supporting platform, and the level of expertise and maturity of the GC consumer organization in operating and maintaining cloud-based information system environments.
3.5 Security Control Implementation
When implementing a GC cloud profile, the CSP is responsible for a large portion of the baseline security controls. However, to meet GC security requirements, there are several security controls that a GC consumer organization needs to implement either fully or partially. Figure 3-3 provides a view of the division of responsibility for security control implementation between the CSP and the GC consumer organization.
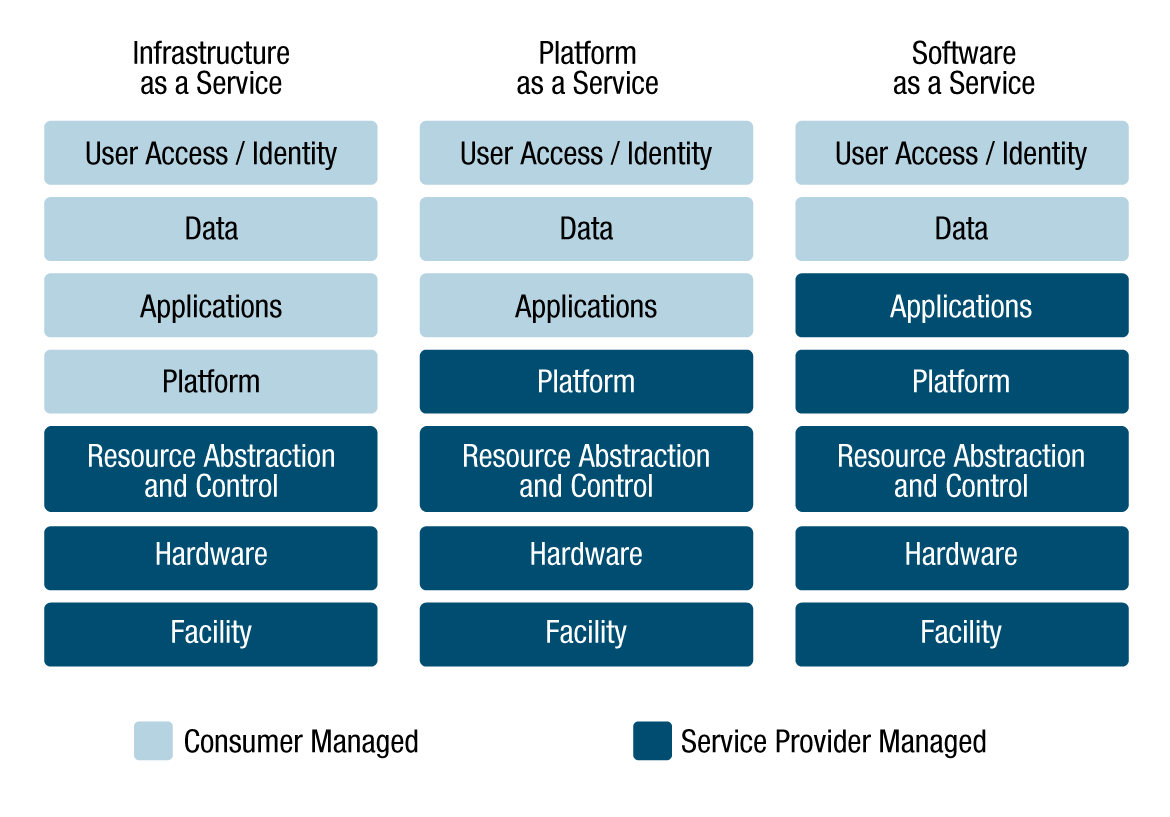
Figure 3-3 - Text version
Scope of responsibility for security controls implemented at the different architectural layers as it applies to the Cloud service models.
Infrastructure as a Service :
- Consumer Managed:
- User Access/Identity
- Data
- Applications
- Platforms
- Service Provider Managed :
- Resource Abstraction and Control
- Hardware
- Facility
Platform as a Service :
- Consumer Managed :
- User Access/Identity
- Data
- Applications
- Service Provider Managed :
- Platform
- Resource Abstraction and Control
- Hardware
- Facility
Software as a Service :
- Consumer Managed:
- User Access/Identity
- Data
- Service Provider Managed :
- Applications
- Platform
- Resource Abstraction and Control
- Hardware
- Facility
The nature of security controls that a GC consumer organization needs to implement in the cloud service is dictated by the service model upon which the GC service is being deployed. For example, if the selected cloud service model is IaaS, the GC consumer organization must implement the security controls of the platform and application layers of the technology stack. These include security controls for access control, audit and accountability, identification and authentication, system and communications protection, configuration management, contingency planning, incident response, maintenance, and system and information integrity. Even under the SaaS cloud service model, the GC consumer organization needs to implement some security controls to manage user access, conduct audits, and respond to incidents.
3.6 Security Assessment and Authorization
Authorization
The ongoing process of obtaining and maintaining official management decision by a senior organizational official to authorize operation of an information system and to explicitly accept the risk of relying on the information system to support a set of business activities based on the implementation of an agreed-upon set of security controls, and the results of continuous security assessmentFootnote 2.
There are different scenarios for implementing cloud-based GC services, each involving different security assessment and authorization scenarios:
- Enterprise information system services: Those information system services provided by a GC department to other GC departments intended on a government-wide basis. Responsibility for security assessment and authorization resides with the business owner or enterprise service organization.
- Departmental information system services: Those information system services sought by departments for the sole purpose of satisfying an internal departmental capability requirement. Responsibility for security assessment and authorization resides with the business owner within the department seeking the capability.
3.6.1 Security Assessment
When implementing a cloud-based GC service, required security controls need to be assessed to establish the extent to which they are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the business security requirements. Understanding the overall effectiveness of security controls is essential in determining and managing the residual risks under which the cloud-based GC service will be operating.
As illustrated in Figure 3-3, the scope of GC cloud profiles includes not just the CSP cloud service infrastructure but all CSP and GC infrastructure components that are used to both provide and consume the cloud-based GC service. As a result, both the CSP and the GC need to conduct security assessments for the security controls that fall within their respective scope of responsibility.
The results of these security assessments are key parts of the documentation package that authorizing officials need to consider to determine whether they should authorize operations of the cloud-based GC service and accept residual risks.
3.6.2 Mapping Security Controls to Existing Certification Programs
Because a GC consumer organization does not have direct control over all the security controls in a cloud-based GC service, or sufficient visibility into the design, development, installation, and assessment of those security controls, alternative security assessment approaches need to be applied. In the GC cloud security risk management approach, this is accomplished by the GC security assessor by taking into account other security assessments that have been conducted, or are in the process of being conducted. Results from these security assessments, if deemed applicable and reliable, are incorporated into the GC security assessments.
In the context of the GC cloud security risk management approach, these security assessments mainly consist of third-party certifications. A third-party certification requires an independent third party that is bound to be objective and apply professional standards to the evidence it reviews and produces. A self-assessment has less value because it is not reviewed by a third party.
GC security control profiles include mapping of existing industry certifications to guide the GC security assessor in associating acceptable evidence to the required security controls.
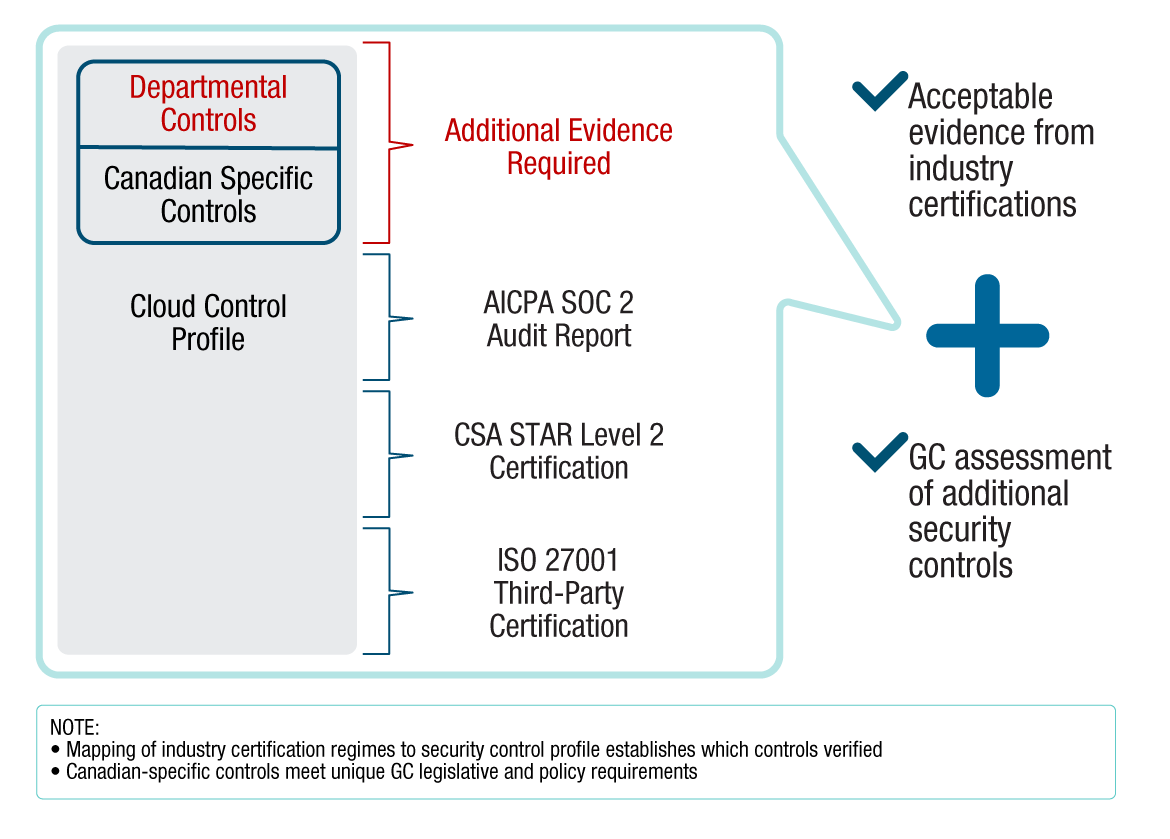
Figure 3-4 - Text version
The GC cloud security risk management approach includes the concept of certification evidence re-use. The GC security control profile for cloud includes mapping of acceptable evidence from industry certifications such as AICPA SOC 2 audit reports, CSA STAR Level 2 Certification, ISO 27001 Third-Party Certification.
The Canadian-specific security controls or departmental controls will require additional evidence and GC assessment of these additional security controls.
3.6.3 Assessment of Additional Security Controls
As illustrated in Figure 3-4, third-party certifications do not cover Canadian-specific security controls selected for GC cloud profiles. As part of the procurement process, additional security requirements and contract clauses may need to be included to ensure that CSPs provide required evidence that can be validated by the GC security assessor. It is expected that standard GC security risk management processes and procedures will be followed when performing these additional security assessment activities.
GC consumer organizations are responsible for the security assessment of the security controls that are allocated to them in the GC cloud profiles. As shown in Figure 3-4, this responsibility extends to any additional security controls being implemented to satisfy departmental requirements. GC consumer organizations are expected to subject these security controls to security assessment activities following standard GC or departmental security risk management processes and procedures.
3.6.4 Stacking of Authorizations
In the cloud space, many cloud systems rely on other cloud providers to provide a comprehensive set of services for the end customer. An example of this is a software provider utilizing an infrastructure provider to deliver a SaaS offering. In this case, the software provider will inherit security controls from the infrastructure provider.
The GC cloud security risk management approach makes allowance for the stacking of authorizations like building blocks. In this model, the authorization for each cloud system must only describe the implementation of that specific system. For example, a SaaS service provider would not specify in its own documentation implementation details or evidence related to the infrastructure service that it leverages. This reduces the number of certifications or security assessments, eliminates redundancy across authorization packages, and keeps authorizations delineated by information system boundaries.
Much in the same way the software provider in the example above relies on the infrastructure provider to deliver services, the software provider also relies on the security implementation and authorization of the infrastructure provider for the software provider’s implementations and authorization. Accordingly, if a CSP has inherited controls, the authorization of that CSP will be dependent on the authorization of the CSP whose controls they inherit and systems they use to deliver the end service.
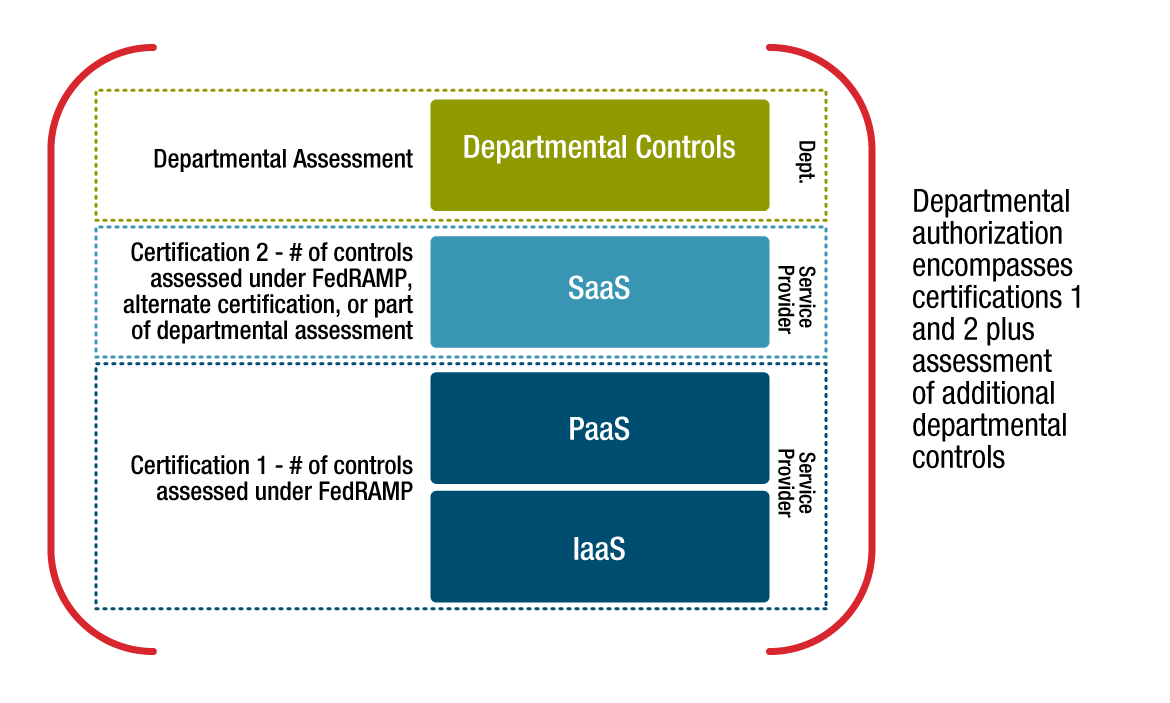
Figure 3-5 - Text version
The authorization stacking use case includes multiple layers:
- For the IaaS/PaaS layer, a number of controls will be a assessed under ISO27001, AICPA SOC2, or an alternate certification or audit as part of the provisional authorization of the service provider.
- For the SaaS layer, a number of controls will be a assessed under ISO27001, AICPA SOC2, or an alternate certification or audit as part of the provisional authorization of the service provider.
- The additional departmental controls will be assessed by the department.
The result is a departmental authorization which encompasses the provisional authorizations plus the assessment of the departmental controls.
3.6.5 Authorization Reuse
A cloud service that has been authorized under an acceptable information system security certification program can be reused from department to department with similar requirements. The service provider blocks in Figure 3-5 represents those services that each GC consumer organization uses and leverages from an authorization perspective. In this view, if another GC consumer organization subscribes to the same cloud services, then the next GC consumer organization would need to confirm that the chosen security profile meets their business needs, and if acceptable, would be required to complete the security assessment and authorization of the departmental components of the information system service.
When granting an authorization at the departmental level, a GC consumer organization must authorize the use of the entire cloud-based GC service, which consists of both the cloud services and the departmental information system service to be hosted on these cloud services. However, if the cloud services have already been authorized for use as part of a cloud-based GC service under the same GC cloud profile, then the GC consumer organization need only worry about the authorization of the GC service component.
3.7 Continuous Monitoring and Authorization Maintenance
The GC cloud risk management approach extends beyond implementation by incorporating activities for continuous monitoring and the maintenance of authorizations during the operational phase of cloud-based GC services. Through continuous monitoring, GC consumer organizations have the necessary capabilities to identify security deviations from the authorization state in both CSP and GC components of cloud-based GC services. Through authorization maintenance, GC consumer organizations have the necessary capabilities to react to these deviations in a timely and effective manner.
4. GC Cloud Security Risk Management Procedures
-
In this section
- 4.1 Roles and Responsibilities
- 4.2 Determine Security Category of GC Service
- 4.3 Select GC Cloud Security Control Profile
- 4.4 Select (or Confirm) the Deployment and Service Models
- 4.5 Assess Security Control Implementation in the Cloud Service Offering
- 4.6 Implement Security Controls in the GC Service
- 4.7 Assess Security Control Implementation in the GC Service
- 4.8 Authorize Operation of Cloud-based GC Service
- 4.9 Operations and System Maintenance
- 4.10 Continuously Monitor and Maintain Authorization
This section describes in more detail, the security risk management procedures that GC departments and agencies, as GC consumer organizations, are expected to complete to procure the right cloud service offerings when implementing or moving GC services to the cloud.
It is recommended that these procedures be integrated within a system development life cycle (SDLC) process as described in Section 5.1.
4.1 Roles and Responsibilities
The table below identifies the roles and responsibilities of various actors as they relate to the security risk management procedures. All roles except for the CSP and third party security assessor are GC or departmental roles depending on the type of information system service being implemented (enterprise, departmental-specific, etc.).
| Security Activities | Roles | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| GC Consumer Organization | GC Security Assessor | GC Cloud Broker | CSP | Third-Party Security Assessor | |||||
| Business Owner | Project Authority | IT practitioners | IT security practitioners | Departmental Security Assessors | |||||
Table 4-1 Notes
|
|||||||||
| 4.2 Determine security category of GC service | R,A | C | C | C | |||||
| 4.3 Select GC cloud security control profile | A,I | R | C | C | I | ||||
| 4.4 Select deployment and service models | A,C | R | C | C | I | C | |||
| 4.5 Assess security controls in cloud service offering | I | A | C | R | R | C | C | C | |
| 4.6 Implement security controls in the GC service | I | A | R | R | C | C | C | C | |
| 4.7 Assess security controls in the GC service | I | A | C | C | R | ||||
| 4.8 Authorize operation of cloud-based GC service | R,A | C | C | C | C | C | C | ||
| 4.9 Operate the cloud-based GC IT service | I | R | R | C | I,C | R | R | ||
| 4.10 Continuously monitor and maintain authorization | A,R,I | R | R | R | R | R | R | R | |
4.2 Determine Security Category of GC Service
Who: Business owner(s) in consultation with IT security practitioners.
What: Determine the security category of the GC service to be hosted on a cloud service.
When: The security category of a GC service is required to determine which cloud deployment model is applicable, and which security control profile is best suited. This activity should occur early during the SDLC process, and is critical to the appropriate procurement and deployment of the right cloud capabilities and deployment models within the GC cloud adoption strategy.
How: Through the sub-activities described below.
A security categorization tool is available to support GC consumer organizations in performing security categorization. This tool provides a standardized methodology to capture the information on business processes and information assets, assess injury levels, and extrapolate a high watermark security category for confidentiality, integrity, and availability.
4.2.1 Identify Business Processes and Related Information Assets
The first step of security categorization is for the GC consumer organization to identify all business processes and related information assets that relate to or will be supported by the GC service. There are several sources from which to identify and describe business processes and related information assets, including:
- Business cases, business impact analysis (BIA);
- Concepts of operations (CONOPS);
- Business functional specifications;
- Department’s program alignment architecture (PAA);
- Enterprise architecture documentation which typically describes an organization’s business processes and related information assets in some detail;
- Discussions or interviews with business analysts and other individuals within related business communities; and
- Treasury Board of Canada Secretariat (TBS)’s Government of Canada Strategic Reference Model (GSRM) Service Reference Patterns Footnote 10 may also be useful in identifying and describing business processes.
4.2.2 Assess Injuries from Threat Compromise
Once the business processes and related information assets have been identified, the GC consumer organization will conduct an injury assessment. GC consumer organizations should assess injury for their business processes and related information assets through a departmental process. This process should use multidisciplinary teams that include representatives from business, legal, access to information, security, and privacy areas.
4.2.3 Determine Security Category of GC Service
By applying the high watermark conceptFootnote 17, the GC consumer organization extrapolates from the injury assessment the security category of the GC service to be hosted on a cloud service. The result is the security category of the GC service.
4.2.4 Document and Accept Security Categorization Results
The GC consumer organization should document and formally accept the results of the security categorization activity. The results can be consolidated in a security categorization report as follows:
- A short description of the related business processes and information assets;
- A description of the expected injuries from threat compromise;
- The levels of expected injury as they relate to confidentiality, integrity, and availability;
- The rationale for attributing the levels of injury;
- The security category of each business activity;
- The security category of the GC service; and
- An explicit statement of acceptance from stakeholders of the security category.
4.3 Select GC Cloud Security Control Profile
Who: Project authority in consultation with IT security practitioners.
What: Select the correct GC cloud security control profile.
GC consumer organizations are expected to select one of the GC cloud profiles, which have been developed specifically for that purpose, and tailor the security controls within their scope of responsibility according to their needs.
When selecting a GC cloud profile, project authorities, with the support of security practitioners, should perform the following tasks:
- Validate the applicability of the business context;
- Validate the applicability of the technical context; and
- Validate the applicability of the threat context.
When: Before the procurement of a cloud service or as part of the selection of an already authorized cloud service offering.
How: After completing the security categorization, the GC consumer organization selects the security control profile that matches the security category of the GC serviceFootnote 18. The GC cloud profiles specify minimum sets of security controls that CSPs and GC consumer organizations need to implement to meet GC requirements defined for specific security categories.
4.4 Select (or Confirm) the Deployment and Service Models
Who: Project authority in consultation with the business owner, GC cloud broker, IT practitioners, and IT security practitioners.
What: The information aggregated during the security categorization step aids the GC consumer organization in selecting the cloud deployment model and service model that best match its internal expertise and required assurance levels.
When: Before the procurement of a cloud service or as part of the selection of an already authorized cloud service offering.
How: Based on GC and departmental information system strategies and the security category of the GC service to be hosted on a cloud service, the GC consumer organization selects or confirms which of the cloud deployment model and service model are best suited. The cloud services availability in the marketplace, the capabilities of these cloud services, the security category of the GC service, as well as other aspects of the information system workloads must all be taken into account when deciding if and when to move to or adopt cloud services.
4.5 Assess Security Control Implementation in the Cloud Service Offering
Who: The GC security assessor in consultation with the CSP and a third-party security assessor. Also the departmental security assessor if the GC consumer organization expects the CSP to satisfy departmental security controls. .
What: Assess the CSP’s implementation of the security controls in the selected GC cloud profile to ensure the appropriate mitigation of threats that could compromise the confidentiality, integrity, or availability of the GC information and services to be hosted on the cloud service. .
When: During the procurement process, an initial high-level security assessment is performed on receipt of vendor response to evaluate bid compliance. Upon vendor selection, a security assessment of the complete collection of assessment evidence and assessment results is performed..
How: The GC security assessor (and departmental security assessor, if required) assesses the implementation of security controls, preferably by examining the security assessment evidence that the CSP has produced as part of another information system service certification program. In the case where security assessment evidence cannot be obtained through independent third-party certification results, the GC security assessor will have to obtain assurance of the proper security control implementation. This may happen in the case when Canadian-specific security controls (and departmental security controls) are not covered by CSP-provided evidence.
To assess the security controls in this situation, security assessors use available guidelines to develop security assessment procedures. Security assessment procedures can be gleaned from different information sources such as NIST’s Special Publication 800-53A, Guide for Assessing the Security Controls in Federal Information Systems and Organizations Footnote 11. The security assessment procedures are then executed and the results documented as part of the security assessment results that will be provided to the authorizer to support authorization.
4.6 Implement Security Controls in the GC Service
Who: IT practitioners and IT security practitioners in consultation with the departmental security assessor, the GC cloud broker, and the CSP.
What: Implement in the GC service the security controls that are required at the layer or layers being implemented.
When: At the scheduled time during the project.
How: Security controls need to be implemented by the project team following the GC consumer organization’s SDLC process. SDLC activities may vary depending on the cloud service model. In most cases, the project team will need to determine the exact set of security controls to implement, specify security configuration, and develop operational security procedures for access control, configuration management, incident response, and auditing. If it is implementing a platform-application over IaaS or an application over PaaS, the project team will also need to incorporate security controls in the GC service design specifications, and develop and test the GC service.
In most cases, the IT project will have to work with the GC cloud broker and the CSP to integrate certain aspects of technical and non-technical security controls to ensure operational visibility and service monitoring.
4.7 Assess Security Control Implementation in the GC Service
Who: Departmental security assessor in consultation with IT practitioners and IT security practitioners.
What: Assess the implementation of the security controls in the GC service (i.e. the GC component of the cloud-based GC service) and any other GC infrastructure components that are used to access and consume the GC service.
When: At the scheduled time during the project.
How: The GC consumer organization conducts security assessment activities as part of the implementation of the cloud-based GC service. Ideally, the security assessment activities are conducted as an integral part of the SDLC process.
4.8 Authorize Operation of Cloud-based GC Service
Who: Business owner in consultation with the project authority, IT practitioners, IT security practitioners and the departmental security assessor.
What: Authorize the use of an enterprise, or departmental cloud-based GC service.
When: While different authorization activities may occur during the project life cycle process (e.g. approve project plan, approve system security controls), this activity represents the risk owner’s decision to authorize a cloud-based GC service for use. It takes place once security assessment activities are completed, and before the cloud-based GC service is declared operational and is available for use.
How: Through the sub-activities described below. Authorization is accomplished as part of the governance and risk management activities to declare information systems operational and hand over from project teams to operational teams.
4.8.1 Define and Document Required Mitigation Activities
The security assessment findings inform the process of identifying gaps and developing recommendations for their treatment. This occurs while taking into consideration the business and risk context, as all services are likely to have deficiencies, and relevant gaps are the ones that can clearly cause harm to the organization. The results of this analysis lead to the establishment of a plan of action and milestones (PoAM) that address how the CSP and the GC consumer organization will correct or mitigate any of the deficiencies with an agreed upon timeline. This information must be incorporated in the authorization package.
4.8.2 Assemble and Submit Authorization Package
Following the preparation of the PoAM, the project team assembles a final package and submits it for authorization review. A final package will include all documents created and referenced during the security assessment activities including additional authorization evidence reviewed for services and components that were inherited by the new information system service. The authorizing official will review the authorization package and make a risk-based decision on whether or not to authorize the cloud-based GC service. The package will include an authorization letter for signature by the authorizing official.
4.8.3 Grant Authorization for the Cloud-based GC Service to Operate
The authorization documentation is meant to document and communicate the authorization decision, any conditions for the operation of the cloud-based GC service in support of departmental business requirements, any required mitigation efforts and plans to achieve these (along with target dates), and is a record of management’s intent for the operation of the service.
4.9 Operations and System Maintenance
Who: IT practitioners, IT security practitioners, and the GC cloud broker in consultation with the departmental security assessor and the GC security assessor.
What: Execute the security controls for their respective components as per their operational responsibilities and agreements.
When: During the operational phase of the cloud-based GC service.
How: The GC consumer organization and the CSP execute security controls through operational security procedures in accordance with established schedules. Operational security procedures cover a wide range of activities, including:
- User accounts, groups, and privileges operations;
- User identifiers and authenticators operations;
- Vulnerability assessments and penetration testing;
- Backup and restoration operations;
- Physical access control operations;
- Storage media operations;
- Configuration and maintenance operations;
- System and security events monitoring and reporting;
- Responding to incidents and contingencies; and
- Auditing operations.
4.10 Continuously Monitor and Maintain Authorization
Information Security Continuous Monitoring (ISCM)
Maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions Footnote 15.
[Note: The terms “continuous” and “ongoing” in this context mean that security controls and organizational risks are assessed and analyzed at a frequency sufficient to support risk-based security decisions to adequately protect organization information.]
Who: Business owner, IT practitioners, IT security practitioners, departmental security assessor, GC security assessor, CSP, and third-party security assessor.
What: The continuous monitoring and maintenance of authorization during the operational phase of a cloud-based GC service. Within the context of the GC adoption of cloud service offerings, the continuous monitoring approach defines how the security controls of cloud-based GC services are monitored over time, how monitoring data is used to determine if these services are still operating within their authorization parameters, and the actions to take when parameter deviations are identified.
For the cloud service component of a cloud-based GC service, the CSP needs to provide to the GC on a regular and recurring schedule, evidence that it maintains its cloud security certifications. The CSP must also provide to the GC a periodic feed of monitoring data for certain aspects of its cloud services. The GC consumer organization needs to monitor the GC service operating on the cloud service as well as the GC infrastructure components that it uses to access and consume the GC service. The GC consumer organization then uses this monitoring data, in conjunction with the monitoring data provided by the CSP, for ongoing authorization decisions as part of its enterprise-wide risk management program.
When: On an ongoing basis throughout the operational period of the cloud-based GC service.
How: Through the sub-activities described below.
During the procurement and operational phase of a cloud-based GC service, the CSP must provide security control assessment evidence through existing cloud security certification programs. The collection of evidence is renewed through the re-certification activities that CSPs must undergo to maintain these cloud security certifications. The GC consumer organization may also reserve the right to engage in security assessment activities, and these arrangements must be documented through contractual agreements.
GC consumer organizations monitor the GC components of their cloud-based GC services through their departmental procedures in compliance with applicable GC policies, directives, and standards.
4.10.1 Operational Visibility and CSP Certification Maintenance
An important aspect of a CSP’s continuous monitoring process is to provide evidence that demonstrates the effectiveness of its security program. CSPs are required to provide evidentiary information to operational authorities at a minimum of annually or the declared certification refresh rate associated with commercial third-party certifications that have been used as evidence of a valid and functioning CSP security program. The submission of this updated certification evidence allows GC consumer organizations to maintain confidence that the CSP are committed to and continuing to protect their information systems in line with the security control profiles under which they were certified. If required, the GC consumer organization maintains the right to evaluate the risk posture of the CSP’s service offering by performing their own security assessment activities targeting either all the security controls in a profile, or a subset thereof.
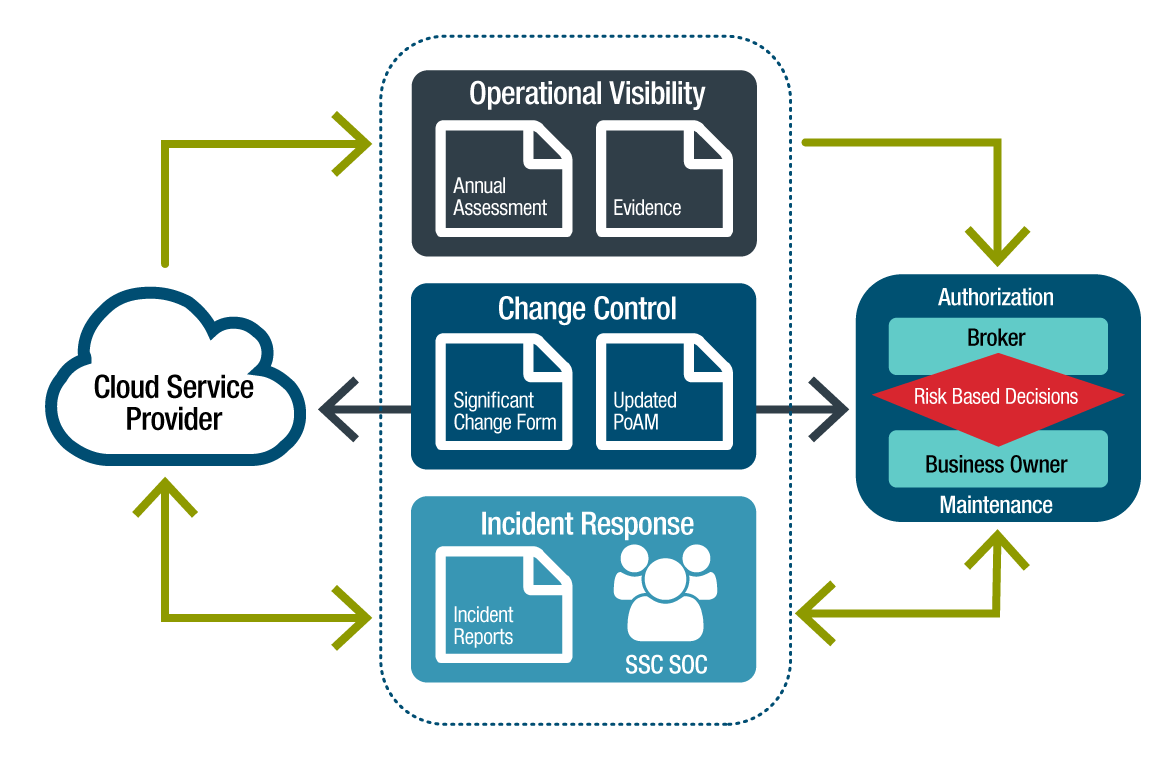
Figure 4-1 - Text version
The continuous monitoring of cloud-based GC service includes various activities between the Cloud Service Provider, and Cloud Broker and/or Business Owner to support risk-based decisions and authorization maintenance including:
- Operational Visibility - evidence and updated annual assessments
- Change Control – significant change forms and updated plan of action and milestones
- Incident Response – engagement with SSC SOC and incident reporting
4.10.2 Change Control
During the operational phase, the GC consumer organization and the CSP need to maintain the security posture of their respective components of a cloud-based GC service through change and configuration management processes and procedures.
Changes during the operational phase of a cloud-based GC service may also require changes to security solutions or may otherwise have an impact on the service’s security posture. Any request for changes should describe the impact that the changes will or may have on security. Where changes are expected to increase residual risks, GC consumer organizations (supported by the CSP, where applicable) should determine if additional security controls and solutions, or additional changes beyond those that are planned, are required to maintain residual risks at acceptable levels. For important changes, GC consumer organizations should, under advice of authorizers, request the assistance of departmental security assessors and the GC security assessor to perform impact assessments.
To manage changes in a secure manner, GC consumer organizations and CSPs should consider the following guidelines:
For routine upgrades or changes to supporting cloud services:
- The CSP’s change control processes (and the associated security controls) must be demonstrated and security impact analysis performed to determine potential impacts to the system. CSPs must be able to provide the change-related information and impact assessment to the GC consumer organization upon request.
For major changes to cloud services:
- Include impact assessments in a formal change request process;
- Require that change requests be approved by operational authorities and authorizers; and
- Optionally, require that an analysis be conducted by a third-party security assessor.
Criteria and thresholds identifying what is considered a major change need to be highlighted in the CSP’s existing service level agreement (SLA), and may be negotiated through the procurement process.
4.10.3 Incident Response
The GC consumer organization and the CSP need to monitor and assess on an ongoing basis the security posture of their respective components of a cloud-based GC service in collaboration with GC Computer Incident Response Team (CIRT) and departmental Information Protection Centres (IPCs). As outlined in the GC Cyber Security Event Management Plan (CS EMP) Footnote 12, cyber security events related to GC information systems, whether located within the GC or within a CSP’s environment, can have a significant impact on the delivery of government programs and services to Canadians and, consequently, confidence in government.
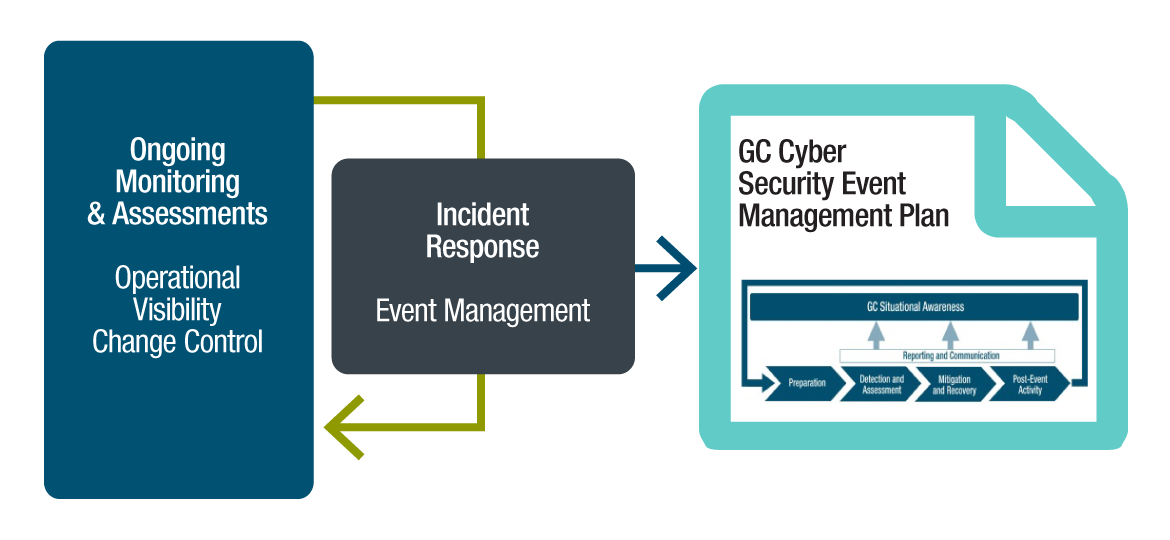
Figure 4-2 - Text version
Incident response for cloud-based GC Service requires ongoing monitoring and assessments as part the operational visibility and change control activities.
This includes incident response activities that are aligned with the GC Cyber Security Event Management Plan.
The GC must continue to have the ability to respond to cyber security events in a consistent, coordinated, and timely manner across the GC. Ongoing monitoring and security assessment are essential processes that help GC consumer organizations detect and respond in a timely manner to attacks, security breaches, and other potentially compromising events and changes within and around the information system’s environment. Ongoing monitoring and security assessment inform the information system security function, as well as incident management, change management, and other operational processes to initiate corrective changes.
To effectively monitor the security posture of their cloud services, CSPs, in support of GC authorization authorities, and in collaboration with security practitioners in the information system security function or an IPC, should perform the following activities:
- Monitor and analyze changes in threats, vulnerabilities, impacts, and risks, and identify the need for changes;
- Monitor the performance and functional effectiveness of security mechanisms and solutions;
- Analyze event records to determine the cause of security events;
- Identify, report, and respond to security incidents; and
- Adequately protect logs, reports, and other monitoring artifacts.
The establishment of security incident management requirements is executed through contract negotiations and may be already in place through CSP SLAs and associated performance targets. After contract award, the implementation of the incident response requirements is executed in line with the appropriate SLAs.
4.10.4 Authorization maintenance
When following the GC cloud security risk management process, a GC consumer organization initially authorizes the operation of a cloud-based GC service as part of the procurement and on-boarding process. Following this, through the continuous monitoring activities described in the previous section, the business owner, supported by IT practitioners, IT security practitioners, and departmental security assessors maintain the authorization state of their cloud-based GC services.
In the context of supporting cloud services, the authorization maintenance process consists of activities where the GC consumer organizations:
- Periodically review the security category of supported business activities;
- Re-assess the threat environment and the security performance of technical environments;
- Review the results of security control performance assessments; and
- Review the activities of CSPs to ensure that they have adequately maintained the security posture of their information systems according to the security provisions of their operations plans.
The outputs of authorization maintenance activities include updated residual risk assessments, updated plans of actions and milestones, and updated security provisions of operations plans.
When the results of authorization maintenance activities show that a cloud-based GC service is no longer operating within acceptable levels of residual risk, there are a range of avenues that GC consumer organizations, in collaboration with the GC cloud service broker and the CSP, can pursue to remediate the situation, including:
- Implementing temporary security measures to protect supported business activities (e.g. disconnect the information system service from the Internet, activate a portion of a contingency plan);
- Updating implemented security controls to correct security deficiencies and return the information system service to its authorized state of operation;
- Accepting the new levels of residual risk; or
- Any combination of these avenues.
If the level of residual risk remains unacceptable after initial remedial actions, authorizers may elect to revoke the authority to operate pending further remedial action. The revocation of authorization would lead to additional security analysis activities to identify specific deficiencies within the operational context, followed by the application of corrective measures or improvements to implemented security controls to return the cloud-based GC service to its authorized state. Appropriate contract clauses must also be developed as part of the procurement process to mitigate potential security risks, including provisions for contract termination if mitigation to an acceptable level is not possible.
5. System Life Cycle Considerations
5.1 SDLC Process
The activities of the GC cloud security risk management process are not meant to be standalone activities performed in isolation from traditional SDLC activities. Rather, this document explains the critical risk management activities that must be completed to leverage cloud services, and expects that these activities will be incorporated in whatever SDLC process a department or service organization has already implemented and uses to develop capabilities.
Figure 5-1 depicts a notional SDLC processFootnote 19 with the GC cloud security risk management activities from the perspective of the cloud broker. In this view, the GC or cloud broker procures a cloud service for the marketplace under an existing security control profile for GC consumer organizations to use for a project seeking cloud services.
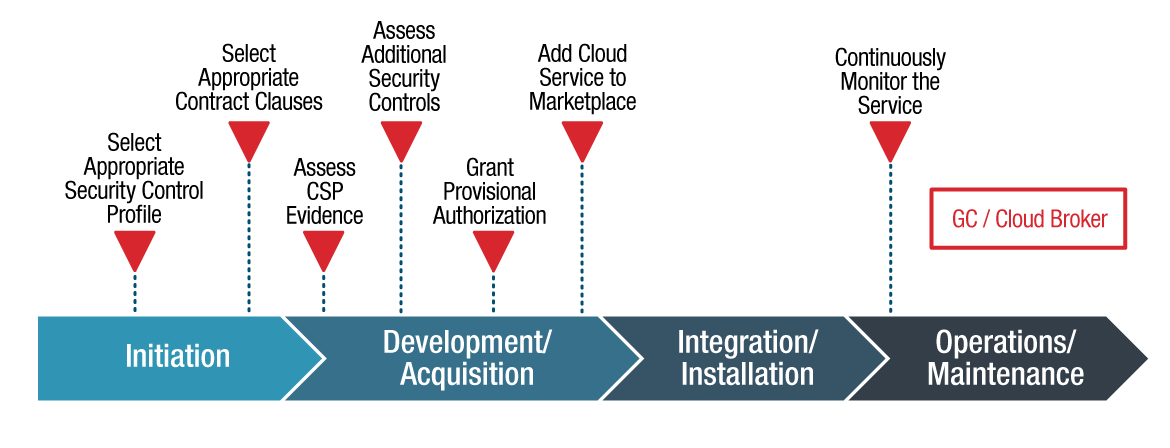
Figure 5-1 - Text version
The notional SDLC process for the GC/Cloud Broker view includes phases with a number of activities:
- Initiation
- Select appropriate security control profile
- Select appropriate contract clauses
- Development/Acquisition
- Assess CSP evidence
- Assess additional security controls
- Grant provisional authorization
- Add cloud service to marketplace
- Integration/Installation
- Operations/Maintenance
- Continuously monitor the service
Figure 5-2 depicts a notional SDLC process from the perspective of a GC consumer organization. In this view, the GC consumer organization selects a suitable cloud service from the marketplace, assesses additional security controls that it expects the CSP to satisfy, and implements and assesses security controls in the GC service.
It is expected that GC consumer organizations will implement and assess security controls in GC services through the execution of a series of engineering, design, development, and security assessment activities across the SDLC process as recommended in Annex 2 of ITSG-33 Footnote 3.
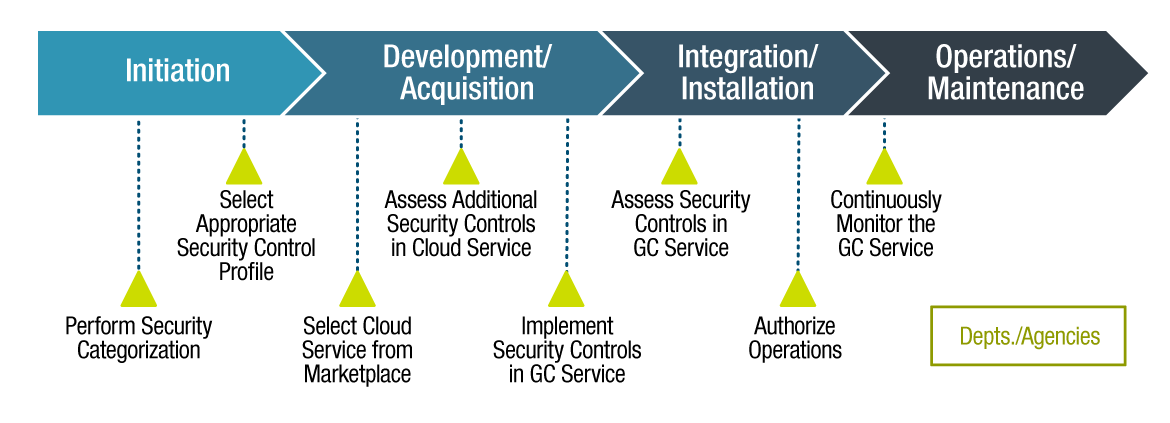
Figure 5-2 - Text version
The notional SDLC process for the Departmental view includes phases with a number of activities:
- Initiation
- Perform security categorization
- Select appropriate security control profile
- Development/Acquisition
- Select cloud service from marketplace
- Assess additional security controls in cloud service
- Implement security controls in GC service
- Integration/Installation
- Assess security controls in GC service
- Authorize operations
- Operations/Maintenance
- Continuously monitor the GC service
5.2 Shared Implementation and Operations Responsibility
When implementing a cloud-based GC service, the responsible GC consumer organization and the supporting CSP are each responsible for the implementation and operations of their portion of the service. This shared responsibility is illustrated in Figure 5-3. In this figure, a GC consumer organization draws from a suitable profile, the baseline security controls that apply to the portion of the GC service being implemented over the cloud service. GC consumer organizations can also use centrally provided services to meet their requirements (e.g. monitoring, incident response, etc.).
From the same profile, the security controls that apply to the CSP are included as mandatory security requirements to procure the underlying IaaS, PaaS, or SaaS cloud service. Following implementation, the GC consumer organization and the CSP are each responsible for operating and maintaining their portion of the cloud-based GC service.
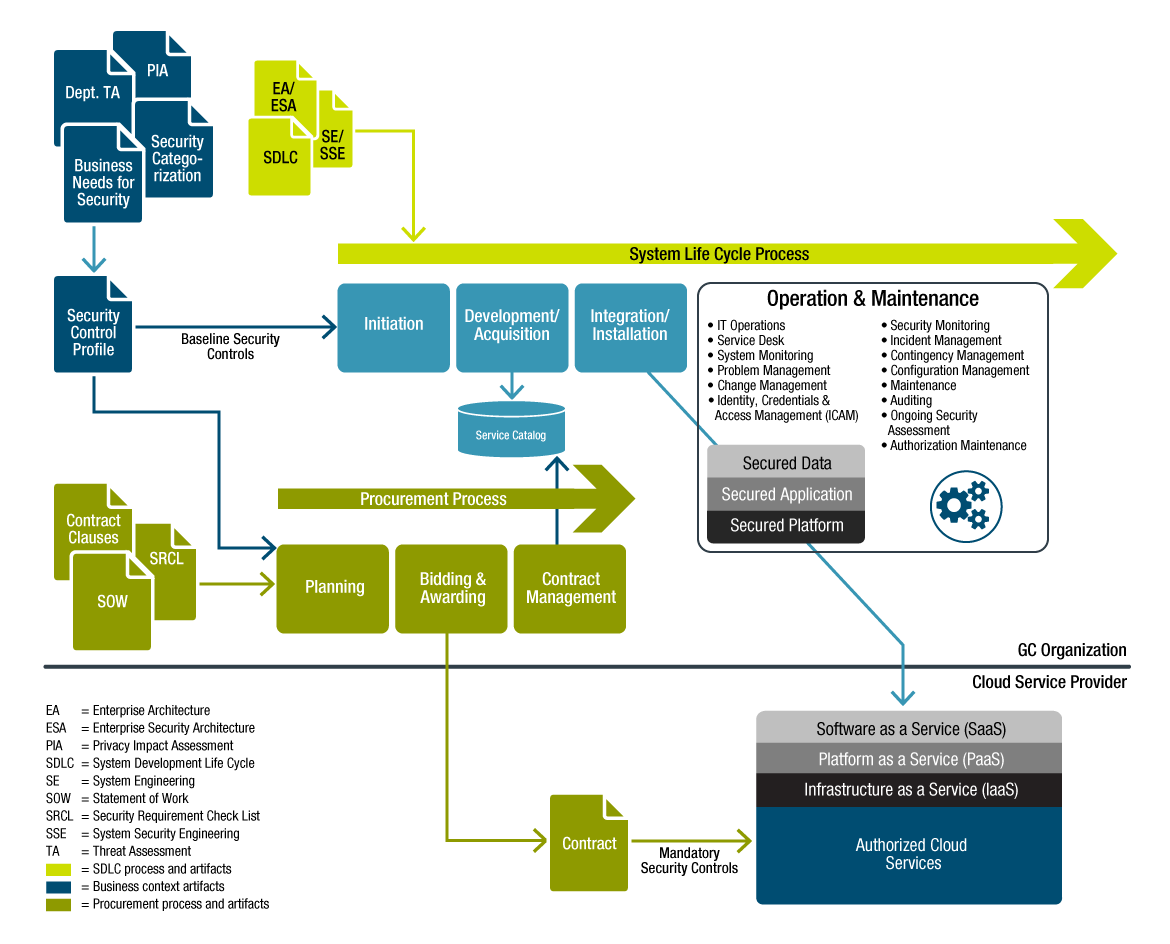
Figure 5-3 - Text version
The shared implementation and operations responsibility includes various activities and inputs:
For the GC Organization, there are two processes the system life cycle process and the procurement process.
The system life cycle process encompasses the systems development lifecycle, enterprise architecture and enterprise security architecture, and system engineering and secure systems engineering in support of the various phases:
- Initiation
- Inputs include the Security Control Profile which is derived from business needs for security, security categorization, privacy impact assessment, departmental threat assessments.
- Development and Acquisition
- Integration and Installation
- Operations and Maintenance
- IT Operations
- Service Desk
- System Monitoring
- Problem Management
- Change Management
- Identity, Credentials & Access Management (ICAM)
- Security Monitoring
- Incident Management
- Contingency Management
- Configuration Management
- Maintenance
- Auditing
- Ongoing Security Assessment
- Authorization Maintenance
This supports secured data, secured application, and secured platform integrated in the authorized cloud services for SaaS, PaaS, and/or IaaS provided by a cloud service provider.
The procurement process encompasses support a number of phases:
- Planning – Includes the statement of work for any required cloud service, standard contractual closes, and a security requirements checklist.
- Bidding and Awarding – results in a Contract Award and mandatory security controls for SaaS, PaaS, and/or IaaS.
- Contract Management
The Cloud Service Provider is responsible for fulfilling the mandatory security controls for SaaS, PaaS, and/or IaaS as part of the Contract for the authorized cloud services.
Figure 5-3 also highlights key inputs. For the system lifecycle process, these include system development life cycle procedures and tools, system engineering/system security engineering procedures and tools, and applicable enterprise architecture/enterprise security architecture artifacts. For the procurement process, key inputs include items such as the statement of work for any required cloud service, standard contractual closes, and a security requirements checklist.
5.3 Security Considerations for Contractual Agreements
As outlined in CSE’s Guidance on cloud security assessment and authorization (ITSP.50.105)Footnote 13, GC consumer organizations must take into consideration security related technical and contractual requirements to reduce security risks as part of the establishment of contractual agreements with CSPs. Key considerations include multi-tenancy, data leakage, data loss, privacy, and supply chain integrity.
GC consumer organizations also need to prepare an exit strategy as part of the contract that will allow the return of applications and data either to the Department or to another provider. GC consumer organizations must also determine the criteria used to invoke the exit strategy (e.g., provider not meeting conditions of the contract or agreement, going out of business, security concerns, etc.). In addition, as part of the contractual agreements, GC consumer organizations should establish the frequency of periodic security assessment and review activities (e.g. review of security incident reports, review of threat environment, and review of operations group security activities).
5.4 Support of Privacy
Under the Directive on Privacy Impact Assessment Footnote 14, GC consumer organizations are required to conduct a privacy impact assessment (PIA) when they are planning to substantially modify government programs and activities involving personal information. A substantial modification includes any change to privacy practices related to activities that are automated by information systems. GC consumer organizations are therefore expected to conduct a PIA when they are planning to implement a cloud-based GC service that involves personal information and ensure that privacy concerns and risks are appropriately mitigated.
GC consumer organization can rely on the GC cloud risk management approach to support those privacy concerns and risks that can be mitigated by information system security. To that end, the GC cloud security control profiles include security controls for protecting the confidentiality, integrity, and availability of personal information. By including a PIA report as input to the SDLC process (as illustrated in Figure 5-3), GC consumer organization will have the opportunity to establish assurance that these security controls have been implemented correctly where required and are operating as expected. PIA reports will also provide GC consumer organizations with the basis for appropriately mitigating all other non-security related privacy concerns and risks.