Guidance on Email Management for Employees
Issue
Email is one of the most common methods of communication in the Government of Canada (GC), creating vast amounts of information that is largely unmanaged. The lack of proper information management (IM) practices related to email impedes effective decision-making, transparency and accountability, and increases the risks related to retention and disposition. Employees need clarification of their roles and responsibilities regarding the information they create, send and receive via email, as well as guidance on ensuring they meet GC requirements when performing cleanup of their email accounts.
Note: For the purposes of this document, the term “Government of Canada employees” includes employees of federal departments as defined in Section 2 of the Financial Administration Act. The advice contained in this guidance, however, could be extended to anyone working for the GC, including casual employees, temporary help, consultants and contractors.
Context
This guidance provides email management best practices for employees in support of section 4.4 of the Directive on Service and Digital. All information created or acquired during the course of employment with the GC, regardless of format or medium, belongs to the Crown. Such information includes email messages. Employees are responsible for determining whether the information they have created or collected in email format is of business value. Most email messages do not have business value and are deemed to be transitory, so they should be deleted as soon as possible. Email that is deemed to have business value must be organized, categorized and stored in a designated corporate repository.
Guidance
Employees should follow their department’s IM procedures for email management. In the absence of formal procedures, employees are encouraged to implement the following best practices, which have also been set out in point form in the Appendix of this document.
- Employees are responsible for managing email messages in their inbox, sent and deleted messages, any folders they have created, and all attachments in their assigned email account.
- In accordance with the Policy on Service and Digital, employees must:
- identify and safeguard email messages according to their security categorization and associated information of business value that has been created, collected and stored during the course of their work
- identify and dispose of transitory email messages
- Employees should transfer email messages that contain information of business value to a designated corporate repository as soon as possible. To ensure the availability of information of business value to all who require it, and to ensure appropriate storage and safeguarding, it is recommended that email messages of business value be transferred to the designated corporate repository within 15 days whenever possible. Additional guidance on identifying and recognizing information of business value can be found in Appendix E of the Guideline on Service and Digital.
Examples of email messages that have business value are:
- messages that reference a decision
- direct communications with clients
- messages that authorize or complete a business transaction where that information is not captured elsewhere (for example, in a financial or human resource system)
- Employees should regularly delete transitory information. Examples of transitory email messages are:
- messages that are copies of information used only for convenience of reference and not as the official record
- messages used for casual communication (for example, meeting invitations, lunch requests, thank you messages)
- informal messages that are not required as evidence in the development of a document
- messages that forward an attachment that is saved in a designated corporate repository
- messages that are duplicate copies of information
- messages received as part of a distribution list or received from a list or other Internet sources, and used solely for convenience of reference
Transitory messages may be deleted once the information is no longer of use. Additional examples of transitory information can be found in the Guidance for Employees of the Government of Canada: Information Management Basics.
-
There are various instances where departments are obligated to search for and provide information. Two notable examples are:
- the legal discovery process
- requests under the Access to Information Act and the Privacy Act
In these and other cases, in accordance with relevant legislative requirements, departments must identify, preserve and collect all information that is responsive to the request.
When a request is received under the Access to Information Act or the Privacy Act, an exact and complete copy of all responsive email messages and attachments must be provided to the department’s Access to Information and Privacy Office. Any transitory email messages that have not been disposed of before a request is received and that are pertinent to the request fall under the legislation and must be treated as any other document and processed as part of the request. It is an offence under section 67.1 of the Access to Information Act to obstruct the right of access by destroying records in anticipation of a request for access under the legislation or during the processing of such a request. Once the Access to Information and Privacy Office has received an exact and complete copy of all email messages and all attachments responsive to a request under the Access to Information Act or Privacy Act, the email messages and attachments may continue to be managed according to their normal life cycle. Information on searching encrypted emails in response to an information request can be found in Appendix B.
- Employees should clean up the contents of email accounts regularly. Spending five minutes daily managing email helps greatly to:
- keep the volume of email information under control
- safeguard departmental information of business value
- share and find information faster
Further information is in the Appendix to assist employees with email cleanup.
- Upon departure from a department, employees should redirect all email messages related to that department to their previous manager.
- Employees who supervise others are also responsible for ensuring that employees who report to them understand and comply with the recordkeeping requirements of the Policy on Service and Digital.
- Employees who manage generic email accounts should apply these best practices to the management of those accounts.
Additional guidance
Employees should consult with their manager when they have questions regarding the management of their email.
For more information on IM, consult the Guidance for Employees of the Government of Canada: Information Management Basics.
Further information
Office of the Chief Information Officer
Treasury Board of Canada Secretariat
Email: ServiceDigital-ServicesNumerique@tbs-sct.gc.ca
Toll-free: 1-877-636-0656
TTY: 613-369-9371 (Treasury Board of Canada Secretariat)
Appendix A: good practices for email clean-up
1. Sort email messages
Email messages can be sorted a number of ways. Use as many ways as possible to facilitate finding and deleting transitory information.
By type of email message
- Meeting invitations and receipts can be deleted.
- Messages received only as a CC (carbon copy) or BCC (blind carbon copy) can be deleted.
By conversation
- Replies: Duplicate information is created in email reply threads, which is transitory and can be deleted.
- Messages in a series: The last email message in a thread contains all the information from the previous email messages. Only the last email message should be kept. Delete all previous email messages in the thread.
- Separate replies: When several recipients have replied separately to an email message, only the original email message can be deleted.
- Requests for information and email messages sent “for information only” purposes can be deleted when they are no longer needed.
By sender
- Email messages from corporate mass mailings and distributions, generic email accounts, and mailing lists or listservs can generally be deleted.
By date
- Sort email messages by date, starting with the oldest. Older messages may be transitory and may be deleted. Verify for business value prior to deletion.
2. Know what email messages to keep
Email messages that contain information of business value must be kept, as set out in the Policy on Service and Digital. Such messages:
- reference a decision of the department
- authorize or complete a business transaction where the information has not been captured elsewhere (for example, in a financial or human resource system)
- communicate directly with clients
3. Move email messages of business value to a corporate repository
Now that your email account is cleaned up, it is easier to keep it organized.
- Transfer email messages that contain information of business value to a corporate repository within 15 days whenever possible and delete transitory information that is no longer required.
- Also remember to manage your email account Sent folder.
- Don’t send attachments. When possible, use links to corporate repositories where documents are stored.
4. Delete transitory email messages
Transitory email messages can be deleted on an ongoing basis as soon as they are no longer required. Caution: Exact and complete copies of transitory email messages that are responsive to an access to information request must be provided to the Access to Information and Privacy Office prior to deletion.
Remember!
- Spending five minutes every day managing your email messages will help you keep your email account organized.
- The email message originator is generally responsible for saving the information of business value to a corporate repository.
- The email message recipient is responsible for saving email messages of business value received from outside the department or agency to a corporate repository.
- Delete transitory email messages as soon as they are no longer needed.
- Delete reference email messages when they are no longer needed.
- Use the email system features such as auto-forwarding rules and alerts to manage email messages. Contact your department’s IT help desk if you need additional help or training.
Appendix B: good practices for searching encrypted emails
When searching encrypted emails for information, a simple keyword search will not do any of the following:
- scan information in the body of encrypted emails
- search the attachments of encrypted emails
In a simple keyword search, encrypted emails will only appear in the search results if the keywords are found in the subject line. Employees should be able to search both the subject line and the content of these emails.
For example, for information that exists as encrypted emails, the content of these encrypted emails must be searchable in order to ensure that any information responsive to an information request are retrieved, in accordance with the Access to Information Act and Privacy Act.
Note that the search function in most email software cannot search text in scanned documents or images.
To ensure that all relevant information in encrypted emails can be identified, it is recommended that departments:
- develop and implement processes and guidance for searching the content of encrypted emails. A sample process for searching the content of encrypted emails in Outlook is provided in part 3 of this appendix. This process:
- is presented as an example of the kind of process that departments should have in place for searching emails
- does not represent the process that they must use
- develop and implement processes and guidance to help users transfer emails of business value, including specific processes for decrypting and transferring encrypted emails of business value, to a designated corporate repository in a timely manner.
- All encrypted emails of business value should be decrypted and stored in a designated corporate repository in a manner appropriate to the security categorization and sensitivity of the information, and in accordance with the Directive on Security Management
- provide training and support to users on the processes for:
- searching the content of encrypted emails in response to information requests
- transferring emails of business value to a designated corporate repository in a timely manner
- follow proper offboarding protocols for IM when employees depart, including decrypting emails of business value and transferring them to a designated corporate repository in a manner appropriate to the security classification and sensitivity of the information
Use case for how to search for encrypted emails in a Microsoft Outlook account
This section provides a sample process for a user-driven search of the content of encrypted emails in an individual’s desktop Outlook account. Newer versions of Outlook may have differences in Outlook’s page design that are not covered in the use case below. Employees using other versions of Outlook may need to follow different instructions to complete Steps 1-5 below.
Consult your department’s IM or information technology (IT) specialists for additional advice for searching encrypted emails (for example, for searching large volumes of encrypted emails).
Step 1: Before you start decrypting emails, verify who has proxy access (that is when another person is able to read, create, or change items in your Outlook mailbox) to your email folders in order to minimize the risk of unauthorized access to the custom search folder that you will create for your decrypted emails.
Step 2: To make encrypted sources of information searchable, set up a custom search folder.
Create a custom search folder in Microsoft Outlook
Creating a custom search folder can help you find emails. The search folder can be set to search any field in an Outlook email. In this case, since we want to look for encrypted emails, you will need to create a custom search folder for encrypted emails.
- To create a custom search folder, open Microsoft Outlook, select the Folder tab on the ribbon, and then select the New Search Folder button.
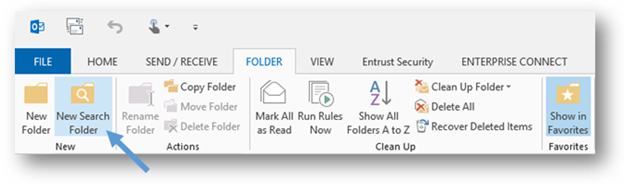
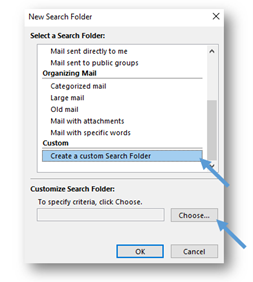
- In the New Search Folder window, scroll down to the bottom of the list. Select the Create a custom Search Folder option, and then select the Choose button.
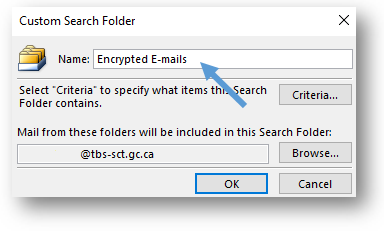
- In the Custom Search Folder window, type in a name for your folder. We suggest “Encrypted Emails.”
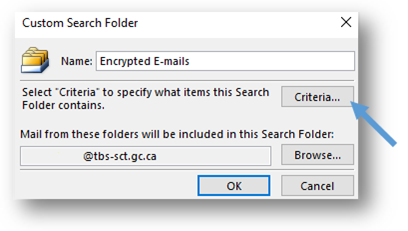
- Configure the criteria for the search. Select the Criteria button and the Search Folder Criteria window will pop up.
- In the Search Folder Criteria window, select the Advanced tab. This tab lets you add criteria based on all the fields that an Outlook email can store.
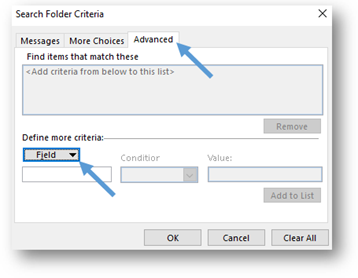
- Select the Field button below Define more criteria and a drop-down menu will appear. From the drop-down menu, select All Mail fields and then Message Class.
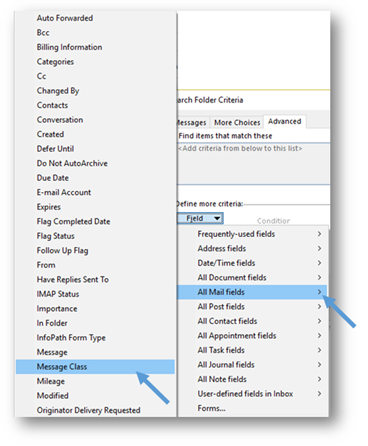
- Under Condition, make sure that the drop-down menu says contains. Under Value, enter IPM.Note.SMIME in the empty field and click on the Add to List button.
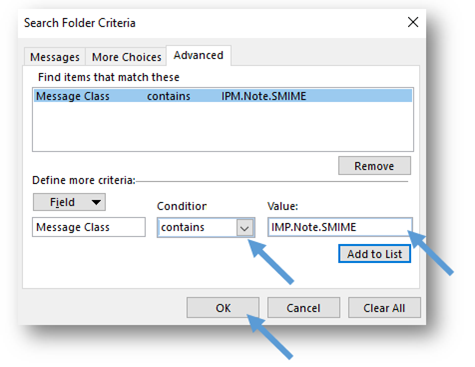
- When you are finished setting the criteria, select the OK button to return to the Custom Search Folder window.
- By default, the custom search that you create will search your entire Outlook mailbox. If you want to conduct a search in specific mailbox, select the Browse button.
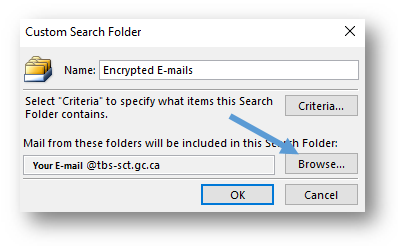
- In the Select Folder(s) window, select the mailbox that you want to include in the search. Select the OK button once you are finished making your selection.
- You will return to the Custom Search Folder window. Select OK.
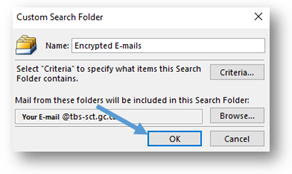
- In the New Search Folder window, select the OK button. Outlook will then create the custom search folder and add it to your Outlook folder list on the left-hand side of the screen. You should be able to see your new Encrypted Emails search folder under the Search Folders heading. The search that you have set up, by following the preceding steps, will be conducted automatically when you select the Encrypted Emails search folder.
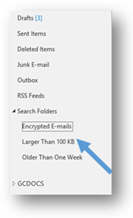
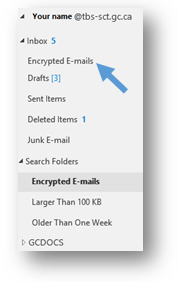
Create an Encrypted Emails subfolder in your Inbox
-
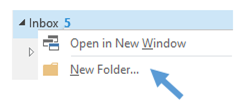
From your Inbox, create an Encrypted Emails subfolder. You can do this by going to the Folder Pane, right-clicking on Inbox and selecting New Folder in the drop-down menu.
The Encrypted Email subfolder in your Inbox is where you will copy your encrypted emails so that you can decrypt them and search the content.
Step 3: Now that you have set up your Encrypted Emails custom search folder and your Encrypted Emails subfolder, you will need to log into Entrust before you can search through your encrypted emails.
- Log into Entrust by doing one of the following:
- selecting the Entrust Security icon
- selecting your Encrypted Email custom search folder or an encrypted email
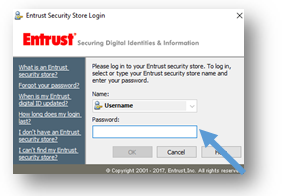
The Entrust Security Store Login window will appear.
- In the login window, enter your password and select OK. You will now be able to read your encrypted messages. *Note: Your Entrust session may timeout and you may be prompted to log back into Entrust.
Step 4: Now that you are logged into Entrust, you will need to copy all of the encrypted emails in the Encrypted Emails custom search folder into the Encrypted Emails subfolder of your Inbox.
- Select all the emails in the Encrypted Emails custom search folder by entering Ctrl + A. Then copy all the emails by entering Ctrl + C.
- Select the Encrypted Emails subfolder in your Inbox and enter Ctrl + V to paste the copied emails into the subfolder.
- There are now copies of all the encrypted emails in your inbox in one folder (the Encrypted Email subfolder in your Inbox).
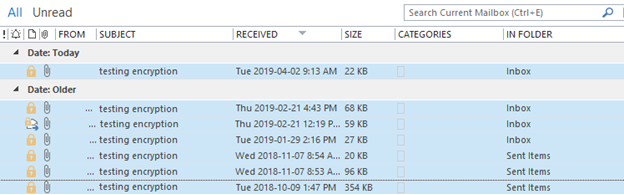
Step 5: Now that all of your encrypted emails have been copied to the Encrypted Emails subfolder in your Inbox, you will need to decrypt them before you can search their contents.
- In your Inbox, go to your Encrypted Emails subfolder and select up to 10 emails to decrypt at a time. To select emails, hold the Ctrl key while you select the emails. Note that you cannot decrypt more than 10 emails at a time.
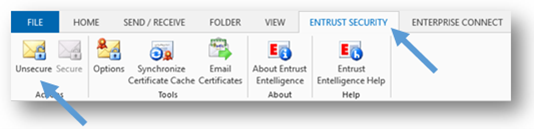
- To decrypt the emails that you have selected, select the Entrust Security tab in the Microsoft Outlook ribbon and select the Unsecure icon. The selected emails are now decrypted. Keep repeating steps 1 and 2 until all the emails in your Encrypted Emails subfolder are decrypted.
- In order to make searching and sorting emails in the Encrypted Emails subfolder visually easier, you make the Message List Pane in Outlook bigger until the search field and drop-down menu in your Outlook are both visible.
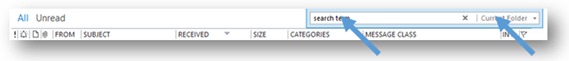
- From your Encrypted Emails subfolder, select the field above the emails that says search Encrypted Email (Ctrl + E), and enter your search term. Ensure that the Current Folder option is selected in the drop-down menu to the right of the field. Relevant results will then be displayed.
- Below the search field and the drop-down menu are column headings. Use the existing columns to help you sort your search results. Some useful headings that you should be able to see include:
- From
- Subject
- Received
- Importance (!)
- Once you have finished preparing your search, you must re-encrypt the emails in the Encrypted Emails subfolder in your Inbox in order to protect this information from potential unauthorized access according to the Directive on Security Management.
- From the Encrypted Emails subfolder, select all emails that you decrypted by entering Ctrl + A. Once you have selected all the emails that must be re-encrypted, select the Entrust Security tab again and click on the Secure button. Doing so will re-encrypt the emails.
- Once you have re-encrypted the emails in the Encrypted Emails subfolder in your Inbox, you should delete this subfolder permanently by selecting the Encrypted Emails folder then pressing the SHIFT + DELETE keys at the same time.
© His Majesty the King in Right of Canada, represented by the President of the Treasury Board, 2024,
ISBN: 978-0-660-73505-4