Internal Audit and Evaluation Bureau - Audit of TBS Pay Controls
Table of contents
Executive summary
In this section
Why does this audit matter?
In May 2017, TBS employees had 3,458 cases in Phoenix. Pay issues escalated to a point in May 2018 where there were 9,135 cases in Phoenix. As of July 2019, there were 5,255 cases in Phoenix.
As of September 2019, 186 TBS employees had emergency salary advances totalling $516,000.
In the 2019 Public Service Employee Survey, the majority of TBS employees reported that they have had a Phoenix issue to either a small or very large extent.
TBS’s Internal Audit and Evaluation Bureau undertook this audit to assess the internal controls administered by TBS, with the goal of ensuring that TBS is supporting employees’ receipt of pay that is accurate and timely.
Audit objective
The objective of this audit was to assess whether pay-related internal controls administered by the Treasury Board of Canada Secretariat (TBS) adequately support timely and accurate pay for TBS employees.
The audit was conducted in accordance with the International Standards for the Professional Practice of Internal Auditing of the Institute of the Internal Auditors (IIA).
Main observations
The audit team concludes with a reasonable level of assurance that TBS has adequate controls in place to support timely and accurate pay for TBS employees:
- all of the data entry reviewed was accurate
- there has been a substantial improvement in timeliness of data entry after the implementation of standards outlined in a memorandum of understanding between TBS and Public Services and Procurement Canada
- 92% of individuals who performed certification of authority (section 34 of the Financial Administration Act (FAA)) had financial delegated authority
- although half of the payments were authorized (section 33 of the FAA) without formal financial delegated authority, such authorizations were compatible with the corporate role of the person authorizing payments
- monitoring controls that are in place to identify pay errors focus mainly on financial risk
- system access to Phoenix is largely appropriate and monitored, and segregation of duties is maintained
- The audit team found that there was a case where system access to PeopleSoft was not properly authorized
Recommendations
- Verify that individuals who sign letters of offer have financial delegated authority (section 34 of the FAA) and that individuals who exercise payment authority (section 33 of the FAA) have financial delegated authority.
- Develop, approve and implement a quality assurance process to monitor pay transactions.
- Continue to monitor human resources transactions based on risk and provide results to Public Services and Procurement Canada and the Office of the Chief Human Resources Officer.
- Strengthen controls for managing access to PeopleSoft.
Statement of conformance
The Internal Audit and Evaluation Bureau has completed an audit of TBS pay controls. This audit conforms to the International Standards for the Professional Practices of Internal Auditing of the IIA, as supported by the results of TBS’s quality assurance and improvement program.
1. Introduction
In 2009, the Government of Canada approved the Transformation of Pay Administration Initiative to address issues with the existing payroll software. The initiative consisted of two main projects: pay modernization and pay consolidation. The pay modernization project included the implementation of the Phoenix pay system. The pay consolidation project included the creation of the Public Service Pay Centre and the centralization of pay operations in Miramichi, New Brunswick. The Pay Centre, which is part of Public Services and Procurement Canada (PSPC), is responsible for managing pay services for 50 federal departments and agencies, including the Treasury Board of Canada Secretariat (TBS).
The Phoenix pay system was implemented at TBS in February 2016. The purpose of Phoenix was to replace outdated technology with a modern pay system that was aligned with industry best practices to allow for faster payments, less paperwork and streamlined processes. PSPC led the implementation of Phoenix. On-boarding of 101 federal organizations to the new pay system occurred in two waves, in February and April 2016.
TBS depends on PSPC for the effectiveness of Phoenix and on the Pay Centre to process timely and accurate pay for employees. TBS’s responsibilities for pay administration are limited to ensuring that the information it provides to Phoenix and the Pay Centre is valid, timely, complete and accurate. Figure 1 illustrates how pay is administered at TBS.
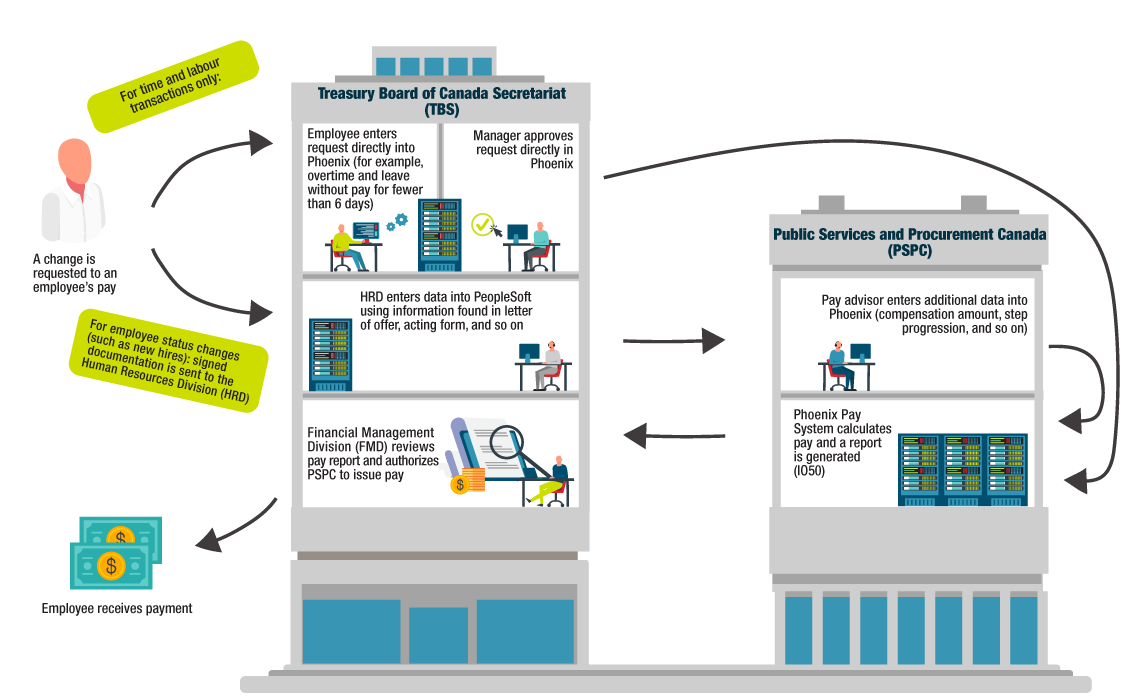
Figure 1 - Text version
Figure 1 illustrates how the pay process is administered at the Treasury Board of Canada Secretariat (TBS).
The process begins with a TBS employee requesting a change in their pay.
What happens next depends on whether the change being requested relates to time and labour or to the employee’s status (such as new hire). The processes are as follows.
Process for time and labour
The first two steps are done at TBS:
- The employee enters the request into Phoenix (for example, overtime or leave without pay for less than 6 days)
- The manager approves the request in Phoenix
The next step is done at Public Service and Procurement Canada (PSPC):
- Phoenix calculates pay and generates a pay report (IO50)
The next step is done at TBS:
- TBS’s Financial Management Division reviews the report and authorizes PSPC to issue the payment.
After that, the employee receives the payment.
Process for employee status changes
The first two steps are done at TBS:
- Signed documentation (letter of offer, acting form) is sent to the Human Resources Division
- The Human Resources Division enters the data into PeopleSoft
The next two steps are done at PSPC:
- A pay advisor enters additional data (for example, compensation amount, step progression) into Phoenix
- Phoenix calculates the employee’s pay and generates a pay report (IO50)
TBS’s Financial Management Division reviews the pay report (IO50) and authorizes PSPC to issue payment.
After that, the employee receives the payment.
In May 2018, PSPC announced a new approach to address pay issues through the use of “pay pods,” which are groups of compensation advisors who are responsible for pay-related actions and are assigned to individual departments and agencies. Pay pods were to gradually take a case management approach where compensation advisors at PSPC would address all outstanding transactions in an employee’s file. The previous approach was to address pay issues by transaction type. The new approach was to ensure more efficient processing of pay and better client service.
In July 2018, TBS and PSPC signed a memorandum of understanding (MOU) to recognize their interdependencies for pay administration. The MOU set out the conditions that govern the implementation and operations of a pay pod that was dedicated to four departments, including TBS. As a department, TBS is responsible for ensuring timely and accurate processing of human resources (HR) transactions, with the goal of minimizing the level of effort required by the pay pod to complete pay transactions and reduce the requirement for post-payment adjustments.
In April 2019, the Office of the Chief Human Resources Officer (OCHRO) developed an implementation plan to improve the timeliness and accuracy of pay. The plan was developed in response to the Office of the Auditor General Fall 2017 Audit Report on Phoenix Pay Problems, which found that departments often could not meet the processing deadlines required by Phoenix, which led to pay errors. The plan introduced standardized timelines for departments for the data entry of 11 types of HR transactions. The purpose of these timelines was to reduce the number of data entries past the effective date of the transaction and to prevent pay errors. These standardized timelines came into effect on April 1, 2019.
2. Audit details
In this section
2.1 Authority
This Audit of TBS Pay Controls is part of TBS’s approved 2019–20 Integrated Audit and Evaluation Plan.
2.2 Objective and scope
The objective of the audit was to assess whether pay-related internal controls administered by TBS adequately support timely and accurate pay for TBS employees.
The audit was identified as a priority engagement based on the risks assessed during the 2019–20 audit and evaluation planning exercise. Since TBS was on-boarded to Phoenix in 2016, employees have experienced issues such as overpayments and underpayments, and in some cases, not being paid at all. Therefore, the purpose of this audit is to ensure that TBS’s Human Resources Division (HRD) and TBS’s Financial Management Division (FMD) are adequately supporting the timely and accurate receipt of pay by TBS employees.
The audit scope covered the period between February 2016 and November 2019.
The audit did not include an assessment of the issuance of emergency salary advances and priority payments to TBS employees.
2.3 Approach and methodology
The audit approach and methodology were risk-based and conformed to the International Standards for the Professional Practice of Internal Auditing of the IIA. These standards require that the audit be planned and performed in a way so as to obtain reasonable assurance that the audit objectives were achieved.
Methodologies to complete the audit work were as follows:
- interviews with management, staff and key stakeholders
- reviews and analysis of documents
- walk-throughs of HRD and FMD processes, testing, and data analytics
3. Audit results
In this section
3.1 Current state
In May 2017, a year after Phoenix was implemented at TBS, there were 1,580 employees who had 3,458 cases in Phoenix. Pay issues escalated to a point in May 2018 where there were 2,788 employees who had 9,135 cases in Phoenix.
For the last three consecutive years, the Public Service Employee Survey asked TBS employees about the extent to which their compensation has been affected by issues with Phoenix. Figure 2 shows that the majority of TBS employees have reported they have had Phoenix issues from either a small to a very large extent since 2017.

Figure 2 - Text version
Figure 2 is a line graph that shows, for the overall public service and for the Treasury Board of Canada Secretariat, the results of the 2019, 2018 and 2017 Public Service Employee Survey for the question, “To what extent has your pay or other compensation been affected by issues with the Phoenix pay system?”
The following table shows the data for the overall public service.
| Response | 2019 | 2018 | 2017 |
|---|---|---|---|
| Not at all |
25% |
29% |
30% |
| To a small extent |
32% |
26% |
24% |
| To a moderate extent |
20% |
20% |
19% |
| To a large extent |
10% |
11% |
11% |
| To a very large extent |
10% |
11% |
12% |
| Don’t know |
2% |
2% |
4% |
| Not applicable |
1% |
1% |
1% |
The total respondents for each year was as follows:
- 2019: 181,161
- 2018: 161,576
- 2017: 174,272
The following table shows the data for the Treasury Board of Canada Secretariat.
| Response | 2019 | 2018 | 2017 |
|---|---|---|---|
| Not at all |
27% |
25% |
28% |
| To a small extent |
31% |
30% |
24% |
| To a moderate extent |
20% |
19% |
23% |
| To a large extent |
11% |
14% |
12% |
| To a very large extent |
9% |
10% |
10% |
| Don’t know |
2% |
1% |
3% |
| Not applicable |
1% |
1% |
1% |
The total respondents for each year was as follows:
- 2019: 1,795
- 2018: 1,381
- 2017: 1,510
In June 2018, the pay pod responsible for TBS began its operations and was introduced as a new approach to stabilize the pay system. Its approach was to manage HR transactions as “new never becomes old,” whereby new transactions are treated first, which minimizes the risk of new transactions becoming old. Figure 3 illustrates the impact of this approach on TBS employees who had cases in Phoenix.Footnote 1
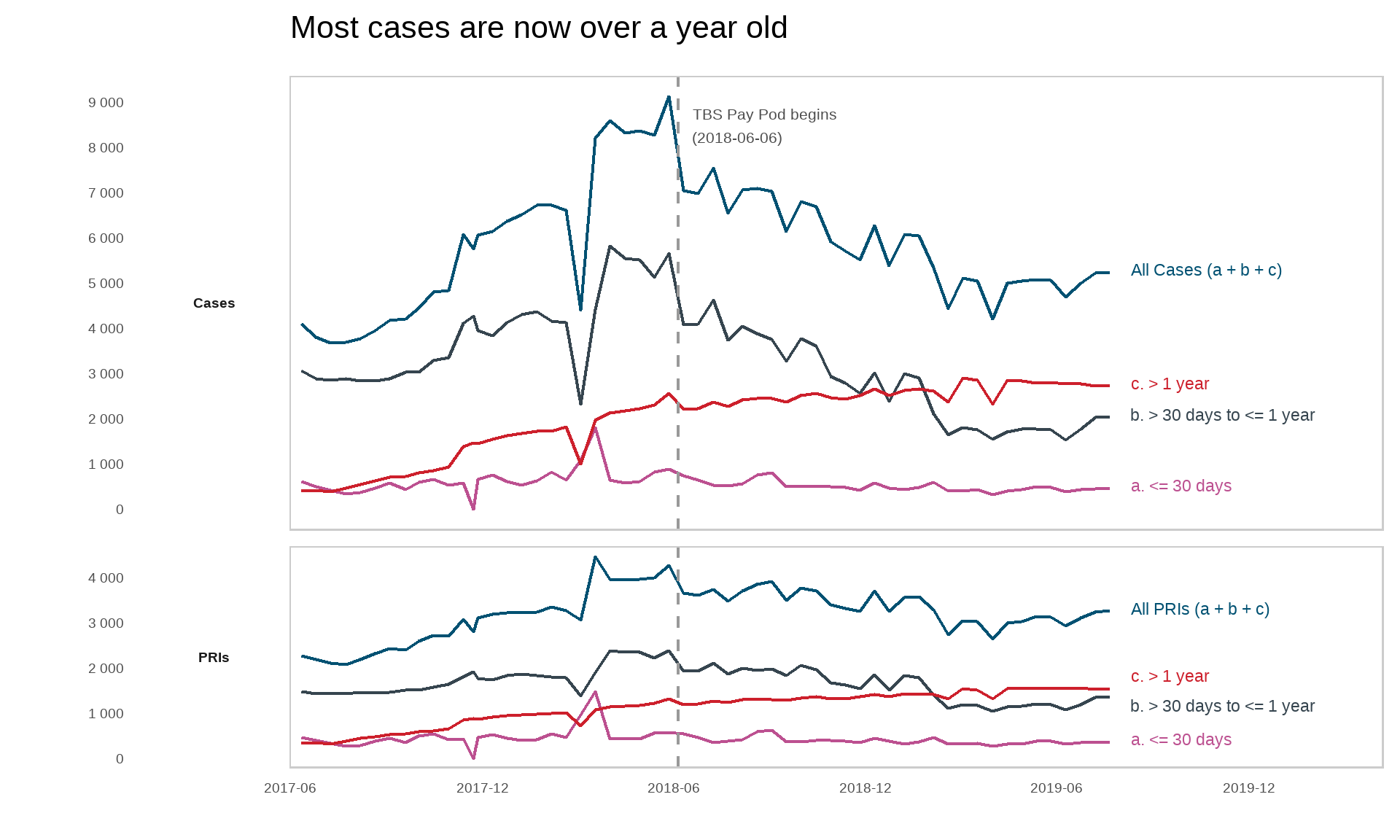
Figure 3 - Text version
Figure 3 is a complex lines graph that indicates, for certain months since 2017:
- the number of active cases that are less than or equal to 30 days old, more than 30 days but less than or equal to 1 year old, and more than 1 year old
- the number of personal record identifiers (PRIs) with active cases that are less than or equal to 30 days old, more than 30 days but less than or equal to 1 year old, and more than 1 year old
A vertical line at June 2018 indicates when the TBS pay pods were introduced.
The following table shows the age of active cases in certain months.
| Month | Number of cases by age | ||
|---|---|---|---|
| 30 days or less | More than 30 days but less than or equal to 1 year | More than 1 year | |
| June 2017 |
612 |
3,073 |
412 |
| December 2017 |
757 |
3,850 |
1,549 |
| June 2018 |
755 |
4,091 |
2,214 |
| December 2018 |
580 |
3,025 |
2,669 |
| June 2019 |
390 |
1,542 |
2,773 |
The following table shows, for certain months since 2017, the number of PRIs with active cases, by age of the case.
| Date | Number of PRIs with active cases, by case age | ||
|---|---|---|---|
| 30 days or less | More than 30 days but less than or equal to 1 year | More than 1 year | |
| June 2017 |
457 |
1472 |
337 |
| December 2017 |
525 |
1743 |
913 |
| June 2018 |
543 |
1928 |
1193 |
| December 2018 |
439 |
1851 |
1419 |
| June 2019 |
315 |
1068 |
1542 |
When the TBS pay pods were introduced in June 2018, total cases between 30 days and 1 year decreased and total cases over 1 year old increased.
Since July 2018, the number of employees who had cases less than a year old has decreased, likely because of the approach to treat new transactions right away. However, the number of cases over a year old increased to the point where, as of July 2019, most cases for TBS employees were over a year old. Therefore, the pay pod approach has been effective for employees who have new cases, but it has not had a meaningful impact on addressing employees’ cases that are older than one year.
As of July 2019, there were 5,255 cases remaining in Phoenix for TBS employees. The number of outstanding cases in Phoenix, in conjunction with the results from the Public Service Employee Survey, support why this audit engagement was important. TBS needs to ensure that it has adequate controls in place to:
- prevent data entry errors
- monitor HR and pay transactions
- verify that system access is appropriate
3.2 Controls to prevent pay errors: data entry
At TBS, PeopleSoft and Phoenix are two critical components of pay administration. Data entry for HR transactions is entered into PeopleSoft by HRD’s data entry team and is uploaded into Phoenix in real time. Such HR transactions include new hires, departures and employees transferring between departments. Data that is not entered into PeopleSoft in a timely or accurate manner may result in a pay issue for an employee.
The audit team reviewed 90 HR transactions to determine whether data entry into PeopleSoft was conducted accurately. The audit team found that all data entry was accurate, but it observed one case where data entry into PeopleSoft did not upload to Phoenix and caused a pay error for an employee.
The audit team reviewed 67 HR transactions (from the sample of 90) to determine whether data entry into PeopleSoft was completed in a timely manner. The audit team observed a marked improvement in the timeliness of data entry transactions since the standardized timelines were put in place on April 1, 2019. There were 31 pay transactions tested for timeliness that occurred before the standardized timelines came into effect; 36 pay transactions were tested that occurred after the timelines were established. Using these standards (generally 10 working days before the effective date of the transaction), timeliness of data entry increased from 3% to 61%. Improving the timeliness of data entry should reduce the likelihood of pay issues for employees. Of the 67 HR transactions reviewed, the audit team found that one HR transaction was entered late into PeopleSoft which caused a pay error for an employee.
Employees enter overtime and leave without pay (less than six days) directly into Phoenix, and fund centre managers are responsible for approving these transactions. The audit team reviewed the data entry of 25 HR transactions to determine the timeliness of data entry by TBS employees and approvals in Phoenix by fund centre managers. The audit team found that five transactions were entered and approved on time, and that these transactions were accurately reflected in the pay period in which they occurred. The remaining 20 transactions were either entered or approved too late by employees or managers to be accurately reflected in the appropriate pay period. Despite the lack of timely data entry, there were no pay issues that had a financial impact on the employees.
Overall, the majority of data entry completed by HRD into PeopleSoft was accurate, and there was a noticeable improvement in the timeliness of data entry.
3.3 Certification and payment authority
The Financial Administration Act (FAA) provides the legal framework for the expenditure of public funds. Section 34 of the FAA provides the certification authority with the authority to certify that the employee is eligible for a payment. In pay administration, section 34 is exercised once a fund centre manager signs a letter of offer to approve payments from their designated fund centre.Footnote 2 A letter of offer, signed by the appropriate fund centre manager, confirms that the employee is eligible for a salary paid by TBS.
Once the letter of offer has been signed by both the fund centre manager and the employee, a trusted sourceFootnote 3 within HRD sends the documentation, accompanied by a Pay Action Request (PAR) Form, to the Pay Centre. The trusted source ensures that all required supporting documentation has been obtained and that the PAR is complete and accurate before the information is sent to the Pay Centre. To minimize pay errors and ensure that pay requests are authorized, only individuals on the trusted source list can send a PAR to the Pay Centre. HRD is responsible for verifying that signatures on the letter of offer are authenticated by a fund centre manager who has delegated financial authority.
Section 33 of the FAA provides the payment authority with the authority to requisition payments. Section 33 is completed by FMD, where payments are verified on a risk-based approach before and after they have been paid to employees. Section 33 is exercised with the purpose of ensuring that payments made to employees are reasonable.
In order to have formal delegated authority, both the certification and payment authorities must have completed and signed forms that outline their responsibilities. Figure 4 illustrates details on section 33 and 34 authorities that are exercised in the hiring process.

Figure 4 - Text version
Figure 4 illustrates the steps involved in approving pay under the Financial Administration Act.
There are 6 steps in all.
The first 4 steps are completed under section 34 of the act:
- Fund Centre Manager exercises section 34 authority by signing a letter of offer
- Letter of offer and other relevant documentation is sent to the Human Resources Division (HRD)
- Human Resources verifies that the staffing request was authorized by a section 34 manager for the appropriate fund centre and completes data entry into PeopleSoft
- The trusted source sends the Pay Action Request and other relevant signed documentation to the Pay Centre
The last 2 steps are completed under section 33 of the act:
- The Phoenix Pay System calculates an employee’s pay based on the inputted data, and the Pay Centre sends a report to TBS’s Finance Division (FMD)
- FMD exercises section 33 of the act by reviewing and approving payments for release
The audit team reviewed 25 PARs and accompanying letters of offer to test the two key controls to:
- determine whether the individual who signed the letter had certification authority (section 34)
- determine whether the individual who sent the PAR to the Pay Centre was on the trusted source list
We observed that all PARs were sent by individuals on the trusted source list. However, two of the letters of offer were signed by individuals who did not have certification of authority (section 34). In both cases, the individuals had financial authority, but not for the fund centres for which they signed. Nonetheless, the audit team noted that in both cases the staffing actions were approved by senior management at TBS.
The audit team reviewed 25 payments to determine whether the individual who performed the payment authority (section 33) had the formal delegated authority to approve the payment to the employee. We found that three individuals who had approved 13 payments in Phoenix did not have the formal delegated financial authority to exercise this authority. Specifically, the signed delegation of authority forms were not completed and signed off by a supervisor. Despite not having formal delegated authority, releasing payments to employees was compatible with their corporate role within FMD.
Awareness of the key controls required as part of certification (section 34) and payment authority (section 33) is necessary to ensuring the proper administration of public funds. Ensuring that those who have payment authority have signed delegated authority forms confirms that payments are reviewed for reasonableness by authorized individuals. Furthermore, verifying that letters of offer are signed by fund centre managers who have appropriate financial delegated authority confirms that the department is paying a salary to an eligible employee.
Recommendation: The Assistant Secretary, Corporate Services Sector, should ensure that (section 33) financial delegated authorities are formalized.
Recommendation: The Director General, Human Resources Division, should inform staff of the necessity to verify that fund centre managers who exercise (section 34) certification authority have financial delegated authority over the position being staffed.
3.4 Monitoring pay transactions to identify pay errors
3.4.1 Account Verification Framework
The Guideline on Financial Management of Pay Administration, issued by TBS and applicable to all of the Government of Canada, outlines a quality assurance process for departments to determine whether pay is reasonable and whether there are significant errors in pay administration.
The quality assurance process includes a review of pay transactions before and after they have been paid to employees. There are two components to the quality assurance process:
- the review conducted by the payment authority (section 33) before and after payments are paid to employees
- a second periodic review of a sample of pay transactions
The scope and frequency of the second review should be risk-based and consider the review conducted by the payment authority (section 33). In addition, the approach to quality assurance must be documented and should be approved by the Chief Financial Officer (CFO).
The audit team reviewed relevant documentation to support the quality assurance process and conducted interviews with staff in FMD to determine whether the process in place aligned with the guideline.
There is a draft Account Verification Framework in place to establish a quality assurance process for TBS. The framework outlines the roles and responsibilities of FMD, HRD and fund centre managers in pay administration. The framework also outlines how risk is to be assessed for various types of pay transactions. Departures and allowances are considered high-risk HR transactions because of the risk of overpayments not being recovered and the manual interventions that are required by the Pay Centre to determine the amount of the allowance. The framework proposes that reviews of pay transactions are to occur quarterly.
The Guideline on Financial Management of Pay Administration states that the level of review performed by the payment authority (section 33) before payments are released will directly impact the level of review performed after the release of payments. The current process is to review all pay transactions above $10,000 before payments are released. Once payments are released, the payment authority reviews all transactions that have a variance of greater than $500 between the last two pay periods. However, these processes are not included in the draft Account Verification Framework. Including the quality assurance work performed by the payment authority (section 33) is important because it informs the scope and frequency of the second quarterly review.
A finalized quality assurance process, once approved by the CFO and subsequently operationalized, will improve the likelihood that pay errors are identified and improve monitoring practices for pay administration.
Recommendation: The Assistant Secretary, Corporate Services Sector, should complete, approve and implement the quality assurance process for pay administration.
3.4.2 Monitoring processes
Monitoring of pay transactions is necessary to ensure that TBS employees are paid accurately and on time. A monitoring framework would increase the likelihood that pay errors are identified and minimize the reliance on employees to determine whether they are paid accurately or not.
The audit team reviewed the monitoring practices that are in place and found that HRD and FMD rely on the following methods to monitor pay transactions:
- FMD receives reports every two weeks from PSPC that list employees who have received payments above $10,000 and employees who have not received any pay. The payment authority (section 33) verifies these payments, with the assistance of HRD, before they are approved.
- The payment authority (section 33) also verifies variances in payments greater than $500 between the last two pay periods after they have been approved.
- Every quarter, TBS (as a department) is required to report to the Office of the Comptroller General on the amount of underpayments and overpayments in order to help build a collective understanding of the financial impact of Phoenix pay issues. To complete this work, FMD analyzes payment variances greater than $5,000 for each quarter and sends a list of identified employees to TBS sectors for review and validation.
- HRD can send four priority cases to the Pay Centre every week. Priority cases are TBS employees who have pay issues that have a high financial impact, such as:
- being paid at the wrong pay increment for several years
- unresolved issues relating to a maternity leave
- accumulated pay problems due to a transfer between departments not having been completed
The Pay Centre reports progress to HRD to monitor the status of the employee’s case.
If a pay error is not identified through these monitoring practices, then it is most likely the employee who self-identifies as having a potential pay issue by contacting either HRD or the Pay Centre.
Current monitoring practices focus largely on the financial risk associated with a pay transaction. To minimize the reliance on the employee, monitoring processes should also identify high-risk pay transactions earlier in the pay process, such as at the point of data entry or when a PAR is sent to the Pay Centre, and track payments to employees to confirm that employees’ pay is accurate and timely.
For instance, monitoring could focus on verifying payments that relate to transactions that require manual adjustments or that have a history of errors. Monitoring could also track employees who have pay issues to determine whether such issues have been resolved. The implementation plan for the MOU between PSPC and TBS requires that TBS review the daily Phoenix IO49 report, which identifies data integrity issues between PeopleSoft and Phoenix. Reviewing this report may have led to earlier identification of the second pay error raised in subsection 3.2 of this report, as data between PeopleSoft and Phoenix had not integrated properly. These approaches to monitoring may help identify pay errors earlier and would supplement existing monitoring controls.
In summer 2019, HRD began monitoring progress against its commitments to implement standardized timelines for the data entry of 11 HR transactions. In particular, HRD was monitoring the timeliness of the data entry into PeopleSoft and reviewing the first pay issued to students to determine whether they were paid accurately. The results demonstrated that students were paid on time but that some payments were not accurate.
Continuing such monitoring, in conjunction with current monitoring practices, would increase the likelihood that pay errors are identified and that TBS employees are paid in a timely and accurate manner.
Recommendation: The Director General, Human Resources Division, should continue to monitor HR transactions based on risk for TBS employees and provide results to PSPC and OCHRO.
3.5 System access
Identity and access management (IAM) is the process of managing who has access to what information over time. IAM is a broad concept that encompasses policies, processes, methodologies and tools to maintain access privileges within an IT environment, including granting access to valid users and denying access to invalid users. At TBS, access privilege includes identifying, tracking, controlling and managing authorized or specified users’ access to the Phoenix pay system and PeopleSoft.
In addition, IAM is used to ensure that appropriate access control policies are in place to protect confidential and sensitive information, such as employee salaries, home addresses and Personal Record Identifiers (PRIs). TBS access controls for pay systems enable:
- user identification and authentication
- restriction of access
- generation of audit trails to prevent improper use or manipulation of pay files and data
These controls ensure that only individuals who have a bona fide purpose and authorization have access to TBS payroll information and data. In short, IAM is a critical component of TBS’s security and compliance protocols as it relates to pay administration.
As such, the audit team reviewed IAM controls for both Phoenix and PeopleSoft, as these systems comprise an essential component of the payroll administration process.
3.5.1 Phoenix
Phoenix has 10 primary business user roles. There are an additional three sub-user roles that can be granted as add-ons to some of the primary business user roles. Phoenix business user roles allow users to access a significant amount of employee data, including personal information that pertains to pay and other HR-related data.
As such, a key privacy requirement for the Phoenix pay system is an emphasis on the protection of personal information and ensuring that access is controlled. Access to Phoenix business user roles should be granted only to employees who require such access in order to perform job-specific tasks.
The Phoenix Security Management Team (PSMT) at PSPC administers access to the Phoenix pay system. These services are administered with the assistance of a large network of Phoenix Security Access Control Officers (SACOs) within client departments. SACOs are client department employees who are the main point of contact between a client department (such as TBS) and PSMT in matters related to providing access to the Phoenix pay system.
At TBS, SACOs are identified and selected by the Manager of Compensation Liaison and HR Systems. The PSMT must be informed when new SACOs are selected. The Manager of Compensation Liaison and HR Systems must complete and sign the Government of Canada Pay System (Phoenix) Security Access Control Officer (SACO) Application Form and send it to PSMT; the individual identified as the new SACO must also sign the form. The form is also used to update or revoke SACO privileges.
Access to Phoenix that is above the standard self-service access is requested via the Government of Canada Pay System (Phoenix) Production Access Request Form (Internal). Access is initiated by a user’s manager, who will indicate on the form the specific role(s) being requested. Both the user and the user’s manager must complete the form and sign it to attest to their understanding of requirements for privacy and security.
Access requests must be reviewed, validated and signed by a SACO prior to being sent to PSMT for processing. In addition, the SACO is responsible for ensuring that access request forms are completed properly and signed by the user and the user’s manager. The SACO will also verify that access being requested is:
- appropriate for the individual based on the individual’s duties and responsibilities
- not in conflict with the user’s existing role(s), whenever applicable
Access management
The industry best practice of “least privilege” suggests that the use of information technology systems should be restricted to the specific components that an employee needs in order to perform their immediate job functions.
As such, the audit team verified whether access to Phoenix was restricted to appropriate personnel. The team made note of the following elements to support their assessment:
- Phoenix user roles and definitions, and the process to manage user access, are available and formally documented
- access for seven users was reviewed, and all seven users were noted to have valid and authorized access to Phoenix that is commensurate with their corporate roles and profiles
The team concluded that a process is in place for granting user access to Phoenix and that this process is working as intended.
Segregation of duties
The audit team verified whether the segregation of duties was maintained and noted the following as elements that supported their assessment:
- user access requests are authorized by the user’s manager and subsequently reviewed and validated by a SACO
- access for seven users was reviewed, and the supporting documentation that substantiated their access was available, i.e., the user, the user’s manager and the SACO had all signed the access request forms
- as mentioned earlier, the seven users whose access was reviewed were noted to have valid and authorized access to Phoenix that is commensurate with their corporate roles and profiles
- a segregation of duties guideline matrix that identifies Phoenix roles that should not be combined is available and formally documented to help support access management of the Phoenix pay system:
- of the seven users whose access was reviewed, we observed no instances of conflicting roles based on the requirements of the segregation of duties guideline matrix
The team concluded that at the time of review, segregation of duties at TBS that are related to the Phoenix pay system was maintained.
Monitoring
The audit team examined whether system access to Phoenix was being periodically monitored for relevance and appropriateness of user access. As part of its review, the audit team made note of the following elements to support its assessment:
- PSMT requested that a yearly exercise be performed by a SACO to verify relevance and appropriateness of user access in Phoenix at a point in time
- as part of the exercise, the SACO would verify that there are no instances of conflicting roles as set out in the requirements of the segregation of duties guideline matrix, and if there are, CFO attestation and endorsement would be sought via the CFO’s signature on the report
The team reviewed the 2018 and 2019 yearly assessments of users’ access performed by TBS SACOs and observed that a handful of users had conflicting roles as set out in the segregation of duties guideline matrix. Access for these users was noted to be supported by CFO attestation as evidenced by the CFO’s signature on the assessment results.
There is also a twice-yearly exercise that is initiated internally by the SACO to verify relevance and appropriateness of user access at a point in time. As part of the audit, we reviewed a twice-yearly exercise performed in 2019 and noted that both the SACO and Manager of Compensation Liaison and HR Systems had signed the report as evidence of their review.
The audit team therefore concluded that a mechanism is in place for the ongoing and periodic monitoring of user access to the Phoenix pay system and that the process is working as intended.
Overall, we have reasonable assurance to conclude that an appropriate framework exists for granting and monitoring user access to the Phoenix pay system. We also have reasonable assurance to conclude that segregation of duties is being maintained and that controls for granting and monitoring user access to Phoenix are working as intended.
3.5.2 PeopleSoft
PeopleSoft is the software used by TBS’s Human Resources Information Management (HRIM) unit. The HRIM unit manages the central agency cluster (CAC) that administers and supports PeopleSoft for a number of government departments and agencies, including TBS.
PeopleSoft contains TBS’s departmental HR information, and its data is used to feed corporate applications such as the departmental phone book and the Phoenix pay system. Given the sensitive nature of PeopleSoft data and the need to maintain data integrity as HR information flows through PeopleSoft to other systems, access to elevated user roles in PeopleSoft should be limited to employees who specifically need it to perform their job functions.
TBS’s HRIM unit manages PeopleSoft access for CAC departments and agencies, including TBS, as part of their administrative and support function for the CAC. These services are administered with the assistance of CAC departmental or agency representatives. CAC representatives are employees who act as the primary point of contact between a CAC department or agency and TBS’s HRIM unit for matters related to providing PeopleSoft access. At TBS, CAC representatives are employees working in the office of HRD’s Director General.
Access to elevated user roles in PeopleSoft is requested via the PeopleSoft User Access Request form. Access is initiated by a user’s manager, who will indicate on the form the specific role(s) being requested. Both the user and the user’s manager must complete the form and sign it to attest to their understanding of privacy and security requirements.
Access requests must be reviewed, validated and signed by a CAC representative prior to being sent to the HRIM unit for processing. CAC representatives are also responsible for ensuring that access request forms are completed properly and signed by the user and the user’s manager. In addition, CAC representatives verify that the access being requested is:
- appropriate for the individual based on the individual’s duties and responsibilities
- not in conflict with the user’s existing role(s), when applicable
In granting access to PeopleSoft, the HRIM unit will first verify that access request forms have been completed and signed by the appropriate parties, i.e., the user, the user’s manager and a CAC representative. In doing so, the HRIM unit performs a secondary check to ensure that access being requested is appropriate for the individual and is not in conflict with an existing role or roles.
Access management
Using the industry best practice of “least privilege” described earlier, the audit team verified whether access to PeopleSoft was restricted to appropriate personnel. During its review, the audit team found that a process is in place for granting user access to PeopleSoft and made note of the following:
- draft documents on PeopleSoft user roles and definitions, and the process to manage user access, are available
- out of five users whose access was reviewed, the team found one instance where a user was granted access to PeopleSoft without valid authorization from their manager, as the access request form had not been signed by the user’s manager but by the user themselves; therefore, no evidence of authorization was available to support the individual’s access to PeopleSoft
As a result, the team made note of two control failures, whereby authorization on the access request form was not adequately reviewed or investigated by (1) the CAC representative or (2) the HRIM unit. As part of follow-up procedures performed to understand the root cause of these control failures, the team found that:
- CAC representatives do not feel that they sufficiently understand the role they are performing, and neither do they feel that they sufficiently understand PeopleSoft user roles, especially regarding making judgment calls on conflicting or incompatible roles
- although the process requires the user, the user’s manager and CAC representatives to understand and carry out their responsibilities regarding the process (evidenced by their signatures on the access request form), the HRIM unit, which is the process owner, is not required to demonstrate or provide evidence of their responsibilities over the process
- as a result, there is a risk that access to PeopleSoft will be granted without adequate review to assess the appropriateness and relevance of roles being granted, which increases the risk of unauthorized access to PeopleSoft and HR data
Recommendation: The Director General, Human Resources Division, should review the process for granting user access to PeopleSoft and ensure that controls are adequately communicated and monitored.
Segregation of duties
The audit team verified whether segregation of duties was maintained and noted the following as elements to support their assessment:
- user access requests are authorized by the user’s manager and subsequently reviewed and validated by a CAC representative and the HRIM unit
- notwithstanding the control failures mentioned above, out of five users reviewed, four users were noted to have valid access and supporting documentation to substantiate their access, i.e., the user, the user’s manager and the SACO had all signed the access request form
- for the one instance of control deviation noted above, the team observed that the process itself still maintained segregation of duties given that (1) the access request was reviewed by a CAC representative and that (2) access was granted by the HRIM unit:
- in addition, authorization for access to PeopleSoft for the user in question was obtained and made available after the fact
- access for five users was reviewed, and all five users were noted to have access that is commensurate with their corporate roles and profiles
The team concluded that at the time of the review, segregation of duties at TBS that are related to PeopleSoft was maintained.
Monitoring
The audit team examined whether system access to PeopleSoft was being periodically monitored for relevance and appropriateness of user access. As part of its review, the audit team observed that a quarterly exercise is performed by the HRIM unit in collaboration with CAC representatives to verify relevance and appropriateness of user access to PeopleSoft at a point in time.
As part of its review, the audit team looked at the June 2019 and September 2019 quarterly assessments and observed that evidence of the reviews having taken place was available in the form of email correspondence between the HRIM unit and CAC representatives.
The audit team concluded that a mechanism is in place for the ongoing and periodic monitoring of user access to PeopleSoft and that this process is working as intended.
Overall, we have reasonable assurance to conclude that an appropriate framework exists for the granting and monitoring of user access to PeopleSoft. It is also our opinion that controls for granting user access are only partially effective; we therefore have identified opportunities for improvement (refer to the observation and recommendation noted above). In addition, the team concludes that controls for monitoring user access are working effectively and that segregation of duties that are related to PeopleSoft are being maintained.
3.6 Overall conclusion
We conclude with a reasonable level of assurance that TBS has adequate controls in place to support timely and accurate pay for TBS employees. There are controls in place to:
- prevent pay errors
- monitor pay transactions to determine whether pay errors have occurred
- ensure appropriate system access to Phoenix and PeopleSoft
Some areas for improvement were identified to strengthen controls administered by TBS to facilitate the stabilization of the pay system.
4. Management response
Recommendation 1
The Assistant Secretary, Corporate Services Sector, should ensure that (section 33) financial delegated authorities are formalized.
| Management Response and Action Plan | Completion date | Office of primary interest |
|---|---|---|
|
Management agrees with the recommendation.
|
|
Directorate of Accounting Services, Financial Management Division, Corporate Services Sector |
Recommendation 2
The Director General, Human Resources Division, should inform staff of the necessity to verify that fund centre managers who exercise (section 34) certification authority have financial delegated authority over the position being staffed.
| Management Response and Action Plan | Completion date | Office of primary interest |
|---|---|---|
|
Management agrees with the recommendation.
|
|
Senior Director, Operations, Human Resources Division |
Recommendation 3
The Assistant Secretary, Corporate Services Sector, should complete, approve and implement the quality assurance process for pay administration.
| Management Response and Action Plan | Completion date | Office of primary interest |
|---|---|---|
|
Management agrees with the recommendation.
|
|
Directorate of Accounting Services, Financial Management Division, Corporate Services Sector |
Recommendation 4
The Director General, Human Resources Division, should continue to monitor HR transactions on a risk-managed basis for TBS employees and provide results to PSPC and OCHRO.
| Management Response and Action Plan | Completion date | Office of primary interest |
|---|---|---|
|
Management agrees with the recommendation.
|
|
Senior Director, Operations, Human Resources Division |
Recommendation 5
The Director General, Human Resources Division, should review the process for granting user access to PeopleSoft and ensure that controls are adequately communicated and monitored.
| Management Response and Action Plan | Completion date | Office of primary interest |
|---|---|---|
|
Management agrees with recommendation.
|
|
Senior Director, Operations, Human Resources Division |
Appendix: audit criteria
| Line of enquiry 1: To determine whether TBS has adequate controls in place to prevent pay errors. |
|---|
|
Audit criterion 1.1: Sufficient pay-related training and guidance is available and taken by Phoenix users to support their roles in pay administration. |
|
Audit criterion 1.2: Employees and fund centre managers submit and approve entries into Phoenix in a timely manner. |
|
Audit criterion 1.3: Data entry into PeopleSoft is performed in a timely and accurate manner. |
|
Audit criterion 1.4: Certification of authority (section 34) is verified before the PAR is sent to the Pay Centre, and the PAR is sent only by an individual on the trusted source list. |
|
Audit criterion 1.5: Payment authority (section 33) is performed in a timely manner. |
| Line of enquiry 2: To determine whether TBS has adequate controls in place to monitor pay transactions and identify whether pay errors have occurred. |
|---|
|
Audit criterion 2.1: TBS has processes in place to monitor pay transactions. |
|
Audit criterion 2.2: TBS has processes in place to identify pay errors. |
| Line of enquiry 3: To determine whether TBS has controls in place to ensure appropriate system access. |
|---|
|
Audit criterion 3.1: System access is restricted to appropriate personnel, and segregation of duties are maintained. |
|
Audit criterion 3.2: System access is monitored for appropriateness on a periodic basis. |