Joint Audit and Evaluation of Privacy Practices at Treasury Board of Canada Secretariat
On this page
- 1. Introduction and authority
- 2. Program background and context
- 3. About the joint audit and evaluation
- 4. Expected outcomes and audit criteria
- 5. Joint results of the evaluation and audit
- 6. Overall conclusion
- Appendix A: management response and action plan
- Appendix B: definitions
- Appendix C: evaluation questions, audit criteria, conclusions and the Treasury Board of Canada Secretariat Access to Information and Privacy Office’s logic model
1. Introduction and authority
-
In this section
- Figure 1: summary of the audit and evaluation
- The importance of this audit and evaluation
- Results and recommendations
- Awareness and understanding of privacy depend on a sector’s previous engagement on privacy activities
- Privacy assessment tools and processes do not embed privacy in a sector’s culture or decision-making
- Resources are inadequate to keep up with the evolving requirements of TBS business
- Management response
- Figure 1: summary of the audit and evaluation
The Internal Audit and Evaluation Bureau of the Treasury Board of Canada Secretariat (TBS) has completed a joint evaluation and audit of privacy practices, which is a function of the TBS Access to Information and Privacy (ATIP) Office. The Internal Audit and Evaluation Bureau has undertaken this evaluation and audit with the help of Goss Gilroy, Inc. and Ernst and Young LLP at the request of the TBS ATIP Office. The evaluation and audit were part of the approved Departmental Evaluation Plan and the Risk-Based Audit Plan.
Figure 1: summary of the audit and evaluation
The importance of this audit and evaluation
Canadians expect the government to respect the spirit and the requirements of the Privacy Act.
The Privacy Policy Unit was established to help TBS meet these requirements.
The Privacy Policy Unit has put in place processes to address privacy requirements and has made substantial progress toward achieving expected outcomes.
Results and recommendations
Awareness and understanding of privacy depend on a sector’s previous engagement on privacy activities
What we recommend
Develop an outreach and engagement plan that includes monitoring mechanisms.
Communicate privacy requirements to sectors that are not regularly involved in privacy activities.
Continue training sectors that have more in-depth or specialized needs.
Privacy assessment tools and processes do not embed privacy in a sector’s culture or decision-making
What we recommend
Re-examine the design and implementation of the privacy impact assessment procedures in consultation with the Office of the Chief Information Officer’s Information and Privacy Policy Division.
Resources are inadequate to keep up with the evolving requirements of TBS business
What we recommend
Supplement the business case with a human resources plan to identify the resources, competencies and skills needed to support the current volume of work and requirements for the future.
Management response
TBS has developed a management response and action plan, which is presented in Appendix A.
2. Program background and context
Privacy in the Government of Canada
Canada’s Privacy Act came into force in 1983.Footnote 1 Its purpose is “to extend the present laws of Canada that protect the privacy of individuals with respect to personal information about themselves held by a government institution and that provide individuals with a right of access to that information.”Footnote 2 Government institutions are prohibited from collecting personal information unless such information is directly related to the delivery of a program or activity for which the institution has parliamentary authority.
“Personal information” is defined in section 3 of the Privacy Act as “information about an identifiable individual that is recorded in any form.” Examples of personal information include a person’s race, age, medical information, financial information and government correspondence. The Privacy Act provides direction to institutions on the collection, right to correction, retention, use, disclosure and disposal of personal information under their control.
Privacy management at TBS
Historically, TBS has collected personal information as part of its role as employer. The information collected includes human resources and people management information about public servants. In recent years, however, the work of TBS has expanded to include outreach and engagement activities, such as social media, surveys and forums. This expansion is a result of the government’s commitment to open government and increased digital access to government data. The expansion has led to a substantial increase in the collection of personal information from both public service employees and the Canadian public.
The Privacy Policy Unit:
- is led by the director of the ATIP Office, who is responsible for both the department’s access to information and privacy activities
- operates under the Strategic Communications and Ministerial Affairs sector
The Information and Privacy Policy Division:
- is a policy centre on privacy practices and access to information
- operates under the Office of the Chief Information Officer
- provides advice and support to other government institutions on issues that concern access to information, privacy and proactive disclosure initiatives
The Information and Privacy Policy Division also participates in monitoring the institutional compliance required in the Access to Information Act and the Privacy Act.
Program activities
The Privacy Policy Unit offers a variety of services including:
- advice on privacy impact assessments, privacy breaches and privacy notice statements
- document reviews
- internal consultations
- training and awareness activities and events
See Appendix B for definitions of the above services.
Roles and responsibilities
The Privacy Policy Unit manages privacy through a suite of policy instruments including:
- the Policy on Privacy Protection
- the Directive on Privacy Practices
- the Guideline for Privacy Breaches
- the Guide to Privacy Breach Management
The Privacy Policy Unit is designed to be an advisory body rather than a monitoring body.
The following parties also play a role in the management of privacy within TBS:
- The Privacy Commissioner of Canada:
- reviews compliance with and adherence to the principles outlined in the Privacy Act
- makes recommendations after reviews or investigations
- The Secretary and/or delegated officials at TBS:
- keep the Privacy Commissioner notified of planned initiatives
- establish privacy protocols for non-administrative purposes
- monitor and report on complianceFootnote 3
- Senior program officials (heads of sectors or branches):
- are responsible for the information that they collect, use and disclose
- must comply with privacy requirementsFootnote 4
Legal Services is engaged in the event that the program or activity is unclear or where potential issues related to the Charter of Rights and Freedoms have been raised.Footnote 5
Functional partners
Functional partners provide expertise and often work with the Privacy Policy Unit to meet client needs when, for example, developing a privacy impact assessment or responding to a privacy breach. The list provided below of functional partners and their responsibilities is not exhaustive, but it does provide insight into how the partners interact:
- Legal Services is responsible for providing strategic legal advice
- Security Services is responsible for marking and classifying documents, safeguarding protected and classified information, and managing assets
- Information Management and Technology and Telecommunications is responsible for the retaining and disposing of authorities
- Procurement and Contracting is responsible for procuring goods and services
- Communications and Ministerial Services is responsible for providing advice and guidance on social media and developing media lines
3. About the joint audit and evaluation
-
In this section
3.1 Objectives
The objective of the evaluation was to assess the performance of privacy practices at TBS. Relevance was not included as TBS has a legislative requirement to implement the Privacy Act. The objective of the audit was to assess the adequacy and effectiveness of privacy practices and controls to support TBS priorities.
3.2 Scope
The joint evaluation and audit scope covered the period from to . Specific documents and data dating back to the 2013 to 2014 fiscal year were examined in order to provide context on program maturity, and additional information received by the team until was considered in analyses.
The joint evaluation and audit did not address:
- information technology: network access, security assessments and authorization protocols
- information management: the retention and disposition authorities for personal information
- document marking and classification
- TBS’s central agency role and the activities of the Information and Privacy Policy Division
3.3 Methodology
The lines of evidence used to inform joint results were proportional to the program’s risk and materiality and included:
- a review of program documentation
- a literature review that examined privacy and its application in government
- a review of administrative data, including testing
- key informant interviews
Due to the low materiality of this joint evaluation and audit, an employee survey was not undertaken. A survey would have been an effective method to fully assess understanding and awareness. The multiple lines of evidence consulted mitigated this limitation.
By conducting the audit and evaluation jointly, the team took advantage of opportunities to reduce duplication of effort. While interviews were conducted jointly, analysis was done separately by the evaluators and the auditors before they came together again to reach joint conclusions and recommendations.
3.4 Statement of conformance
The Joint Evaluation and Audit Privacy Practices Report was undertaken:
- in accordance with the Treasury Board Policy on Results and Policy on Internal Audit
- in conformance with professional standards for evaluation and internal audit
The reporting was supported by the Internal Audit and Evaluation Bureau’s quality assurance and improvement program.
4. Expected outcomes and audit criteria
The evaluation assessed the extent to which the following outcomes were achieved by the Privacy Policy Unit:
Immediate
- Employees, managers and sector heads understand their respective roles and responsibilities regarding privacy
- Employees, managers and sector heads are aware of privacy risks and the impacts of privacy breaches
Intermediate
- Employees, managers and sector heads address privacy risks in decision-making
Long-term
- Privacy awareness is embedded in the organizational culture
The audit examined governance, risk management and controls. The following criteria, with regard to the work conducted by the Privacy Policy Unit, were examined:
- roles, responsibilities and accountabilities
- resources and succession planning
- training and awareness
- the privacy impact assessment process
- the privacy breach management process
- the tools for decision-making
See Appendix C for:
- a comparison of the evaluation questions and conclusions and the audit criteria and conclusions
- the specific elements of the Access to Information and Privacy Office’s logic model that were addressed in the audit and evaluation
5. Joint results of the evaluation and audit
5.1 Privacy awareness
Expected outcome: Employees, managers and sector heads understand and are aware of their respective roles and responsibilities with regard to privacy.
Conclusion: Privacy awareness and understanding across TBS is inconsistent and depends on the extent to which a sector has been engaged in privacy activities.
5.1.1 Why is this important?
Lack of awareness and understanding of privacy requirements and the associated roles and responsibilities could:
- contribute to the improper or unauthorized collection, use, disclosure, retention or disposal of personal information
- lead to unnecessary resource use in the case of over-reporting
5.1.2 Recommendation
The Privacy Policy Unit should:
- develop a formal outreach and engagement plan
- include mechanisms to monitor the effectiveness of the plan
- expand its promotional efforts to ensure that:
- privacy requirements are communicated to those sectors that are not regularly involved in privacy initiatives
- training continues to be offered to sectors that have more in-depth or specialized needs
5.1.3 Findings
Privacy Management Framework
TBS has created a Privacy Management Framework, which has been posted on the TBS InfoSite. The InfoSite is accessible to TBS employees only. This framework supports TBS practices with regard to the creation, collection, retention, use, disclosure, accuracy and disposition of personal information under TBS control. The framework includes the following guidance materials:
- a Code of Privacy Principles
- a Guide to Privacy Breach Management
- an Internal Privacy Breach Report Form
- a Privacy Impact Assessment Framework
- a Privacy Impact Assessment Checklist
These guidance materials were found to reflect the key elements of privacy protection contained in the Privacy Act and supporting policy and directive. Roles, responsibilities, and procedures and protocols for privacy practices are adequately defined and documented.
Understanding and awareness of privacy requirements, including privacy breaches
Interview results showed that understanding of privacy roles and responsibilities varies according to the degree to which individuals have been involved in privacy activities.
Administrative data showed that the majority of TBS sectors have engaged the Privacy Policy Unit at some point during the period examined (2013 to 2018). Figure 2 shows the number of individual privacy services received by TBS sectors. While the majority of TBS has had some interaction with the Privacy Policy Unit, approximately one third interact with the Privacy Policy Unit more regularly. The program data is consistent with interview results, which indicate that awareness varies across the department.
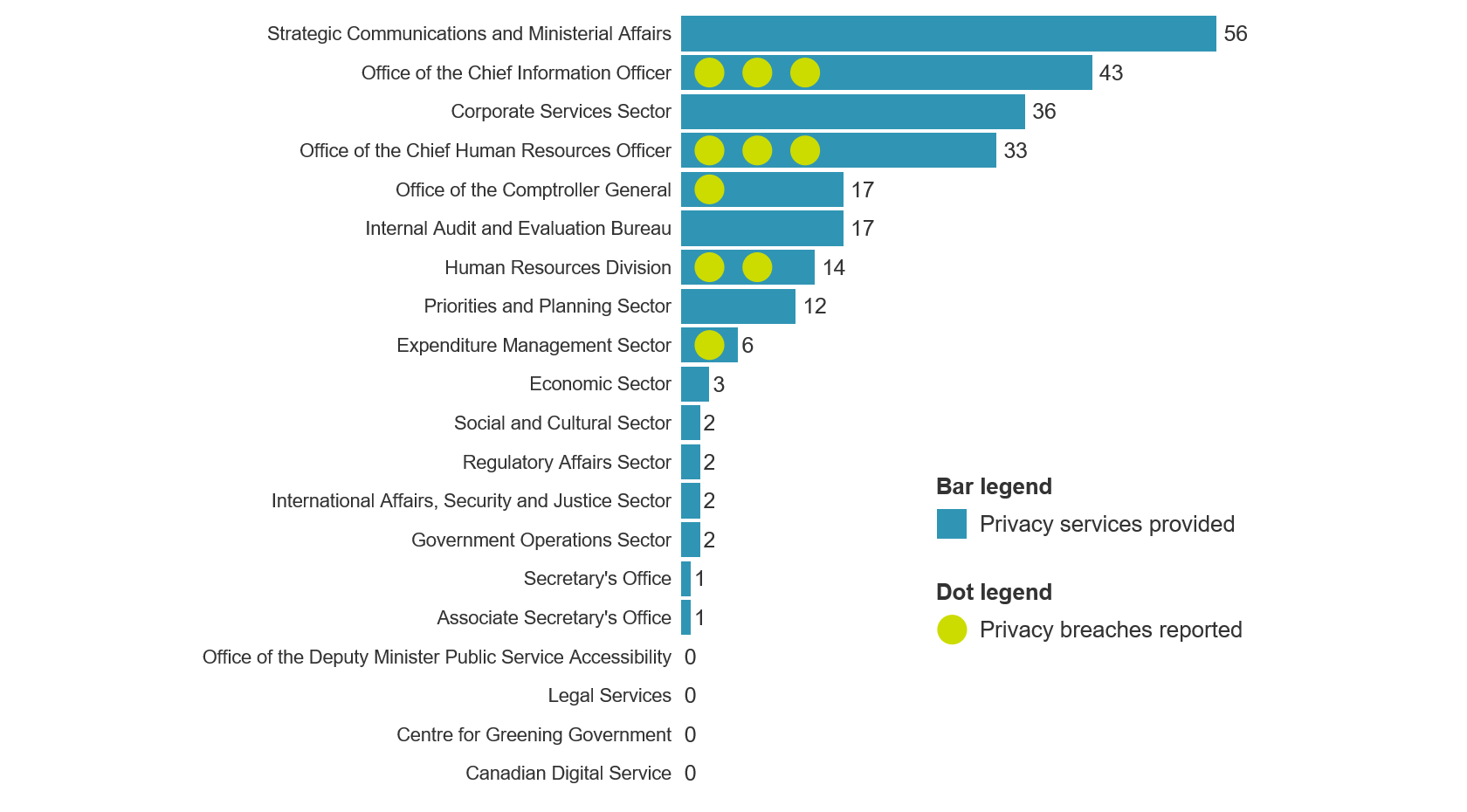
Figure 2 - Text version
Figure 2 is composed of a bar graph that indicates the number of privacy services provided to each sector and dots that indicate the number of privacy breaches reported by each sector.
| Sector | Number of privacy services provided by the Privacy Policy Unit | Number of privacy breaches reported |
|---|---|---|
| Strategic Communications and Ministerial Affairs | 56 | 0 |
| Office of the Chief Information Officer | 43 | 3 |
| Corporate Services Sector | 36 | 0 |
| Office of the Chief Human Resources Officer | 33 | 3 |
| Office of the Comptroller General | 17 | 1 |
| Internal Audit and Evaluation Bureau | 17 | 0 |
| Human Resources Division | 14 | 2 |
| Priorities and Planning Sector | 12 | 0 |
| Expenditure Management Sector | 6 | 1 |
| Economic Sector | 3 | 0 |
| Social and Cultural Sector | 2 | 0 |
| Regulatory Affairs Sector | 2 | 0 |
| International Affairs, Security and Justice Sector | 2 | 0 |
| Government Operations Sector | 2 | 0 |
| Secretary’s Office | 1 | 0 |
| Associate Secretary’s Office | 1 | 0 |
| Office of the Deputy Minister Public Service Accessibility | 0 | 0 |
| Legal Services | 0 | 0 |
| Centre for Greening Government | 0 | 0 |
| Canadian Digital Service | 0 | 0 |
Figure 2 also shows which sectors have reported privacy breaches. Program data is consistent with interview results on awareness, which indicated that privacy awareness increased after employees engaged the Privacy Policy Unit to identify a privacy concern, assess the concern and take action.
Between the 2016 to 2017 fiscal year and the 2017 to 2018 fiscal year, 10 privacy breaches were reported within TBS. To date, when privacy breaches do occur, they have been reported as:
- unintentional
- a result of human or technological error
Upon review, all 10 breaches were deemed by the Privacy Policy Unit to be non-material.
The Privacy Policy Unit suspects that privacy breaches at TBS are over-reported. However, as noted by some interviewees, it is difficult to determine whether the over-reporting stems from a lack of understanding, or whether it indicates risk aversion. A lack of understanding of privacy requirements makes both over- and under-reporting of breaches more likely.
Outreach and engagement, including training
A large part of the Privacy Policy Unit’s day-to-day operations involves providing privacy advice to sectors. Staff at the Privacy Policy Unit estimate that they spend a quarter of their time on reviews and consultations related to the privacy needs of various sectors.
Staff estimate that another 5% of their time is spent delivering presentations to raise awareness at TBS. Presentations are given upon request or in response to a privacy breach. For example, a general presentation on privacy management was provided to all TBS executives in order to raise awareness and support sound privacy management across the organization.
An estimated 10% of staff time is spent developing tools for use at TBS. These tools are posted on the TBS InfoSite, which is accessible to TBS employees only.
Almost all interviewees felt that they received excellent service when communicating with the Privacy Policy Unit. The unit is often sought out by the Office of the Chief Information Officer’s Information and Privacy Policy Division and other departments and agencies for their expert advice on designing and delivering privacy services in the federal government. Interviewees also noted the informal network that the unit has built with its functional partners, which has helped to ensure that consultation occurs on potential privacy issues where needed.
While outreach and engagement activities are evident, the Privacy Policy Unit acknowledges that more awareness is needed based on what they have learned from networking within TBS and from other ATIP functions in the government.
Best practices according to the generally accepted privacy principlesFootnote 7 suggest that privacy training for all employees should be done annually. Such a training schedule is not currently in place at TBS.
Interviewees noted that awareness could be improved by:
- delivering customized privacy presentations to small groups that are repeated consistently in order to keep the privacy conversation alive
- creating daily reminders that embed privacy in day-to-day business
5.2 Ability to support decision-making and embed privacy in TBS culture
Expected outcome: Employees, managers and sector heads address privacy risks in decision-making and privacy is embedded in the organization’s culture.
Conclusion: Improvements can be made to the privacy impact assessment process and tools to effectively identify, manage and report on privacy risks.
5.2.1 Why is this important?
Privacy risks and implications may not be fully considered before a new or modified program or activity involving personal information is established, which could result in improper collection, retention, use and disclosure of personal information and lead to a privacy breach.
Since there is no monitoring of privacy risk and mitigation strategies, there is no way to objectively assess whether privacy risks are under- or over-reported, which in turn affects management’s ability to make informed decisions.
Canadians expect the government to protect their personal information by respecting the spirit and requirements of the Privacy Act. Doing so is essential to maintaining public trust.
5.2.2 Recommendation
The Privacy Policy Unit should re-examine the design and implementation of its privacy impact assessment procedures in consultation with the Office of the Chief Information Officer’s Information and Privacy Policy Division.
5.2.3 Findings
Privacy impact assessment process
The document and data review indicated that the Privacy Policy Unit’s Privacy Impact Assessment Framework reflects the key elements outlined in the Treasury Board Directive on Privacy Impact Assessment.
Privacy impact assessments were not, however, completed in a timely manner. Interview results showed that most were not completed before a new or modified program was established as required by the Directive on Privacy Impact Assessment. On average, it takes 3.5 years to complete a privacy impact assessment at TBS.Footnote 8 While there are no set timelines in the Privacy Act or in the accompanying policy instruments, there is a requirement in the Directive on Privacy Impact Assessment that the process to develop and approve privacy impact assessments should be commensurate to the level of risk.Footnote 9 The long timelines associated with completing a privacy impact assessment may increase the risk that a project may not be completed within envisaged timelines. Figure 3 shows how long it took to conduct privacy impact assessments by project and sector.
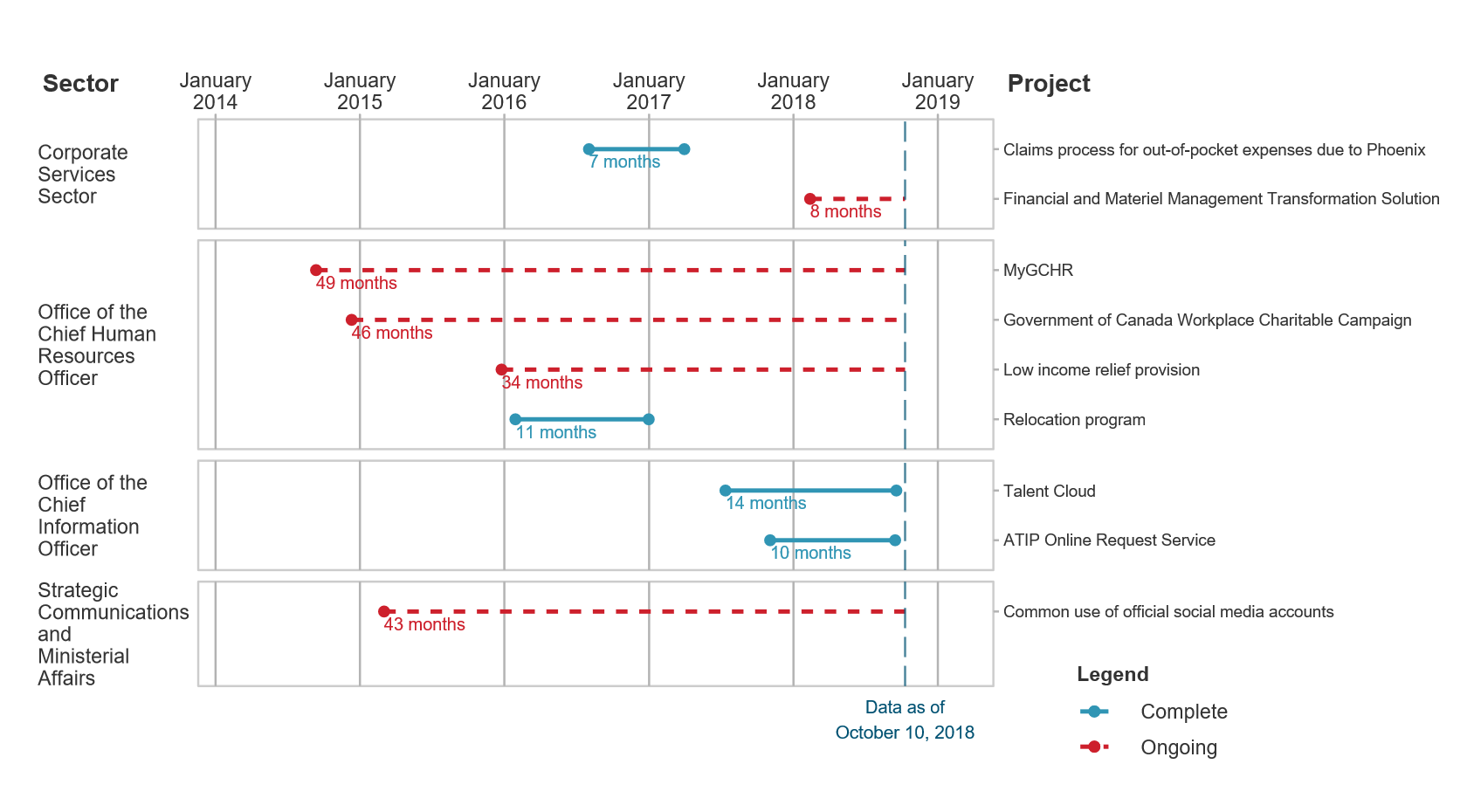
Source: Privacy Policy Tracker
Time to complete selected privacy impact assessments, by TBS sector and project - Text version
Figure 3: time to complete selected privacy impact assessments, by TBS sector and project
Figure 3 is a complex chart that indicates:
- specific sectors and projects
- how long it took for a project to undergo a privacy impact assessment
- whether a given privacy impact assessment is ongoing (as of October 10, 2018)
| Sector | Project | Time to complete a privacy impact assessment | Assessment completed or ongoing (as of October 10, 2018) |
|---|---|---|---|
| Corporate Services Sector | Claims process for out-of-pocket expenses due to Phoenix | 7 months | Completed |
| Financial and Materiel Management Transformation Solution | 8 months | Ongoing | |
| Office of the Chief Human Resources Officer | MyGCHR | 49 months | Ongoing |
| Government of Canada Workplace Charitable Campaign | 46 months | Ongoing | |
| Low income relief provision | 34 months | Ongoing | |
| Relocation program | 11 months | Completed | |
| Office of the Chief Information Officer | Talent Cloud | 14 months | Completed |
| ATIP Online Request Service | 10 months | Completed | |
| Strategic Communications and Ministerial Affairs | Common use of official social media accounts | 43 months | Ongoing |
Interviewees cited limited privacy risk awareness in some sectors, which can lead to late identification of privacy impact assessment requirements, and the administrative burden of the privacy impact assessment process (that is, the rigorous and labour intensive process that often requires hiring external consultants) as inhibiting the timely completion of privacy impact assessments.
Interviewees highlighted three ways in which the privacy impact assessment process could become more efficient:
- TBS should combine risk assessments across all functional partners where possible (for example, privacy, information management and information technology, security). Currently, these assessments are managed in silos. A combined assessment, managed through a single-window:
- could systematically identify the necessary functional partners in the design phase
- would avoid key partners being inadvertently omitted and provide assurance that risks are monitored once the project is in operation
- TBS should re-examine the privacy impact assessment template to reduce the complexity of the assessment and the time it takes to complete the assessment. The following examples show that the gap between privacy requirements and the needs of agile initiatives can be bridged even if legislation is outdated and outside the Privacy Policy Unit’s control:
- Talent Cloud is completing a privacy impact assessment in stages in order to satisfy privacy considerations within shorter time frames
- The Canadian Digital Service has created a framework and online tool that proactively considers key privacy variables that impact users when conducting research or product testing
- TBS should create an annotated privacy impact assessment as a guide to clarify the process and the relevant roles and responsibilities.
Privacy breach management process
The departmental Guide to Privacy Breach Management:
- outlines processes and protocols
- defines key roles and responsibilities for managing privacy breaches
- reflects key elements of the government-wide Guidelines on Privacy Breaches and the Privacy Breach Management Toolkit
The sampled breach reports were observed to be complete, compliant and consistent with the government-wide Guidelines on Privacy Breaches and the Privacy Breach Management Toolkit. Sector representatives who were involved with breaches indicated that the services provided by the Privacy Policy Unit were effective and efficient.
Enable management to be informed about privacy risks and risk exposure for decision-making processes
The literature review,Footnote 10 which included best practices, showed that three actions give rise to effective privacy management within an organization. The three actions are:
- limit the collection of personal information to a need-to-know basis
- ensure that incidents are reported to the appropriate parties
- consult with privacy professionals early and throughout
The Government of Canada’s approach to privacy shares commonalities with other jurisdictions. The norm is to implement privacy management frameworks and tools, including privacy impact assessments and protocols, to manage privacy breaches.
Within TBS sectors, privacy concerns are managed on a case-by-case basis. The privacy impact assessment and privacy breach report are the key mechanisms used to address privacy issues. The process for completing a privacy impact assessment or addressing a privacy breach requires the sector to obtain advice from the Privacy Policy Unit and functional partners (where warranted).
Incentives to seeking privacy advice were:
- uncertainty regarding the presence of a privacy issue, sometimes driven by a need to avoid potential media attention
- a functional partner’s advice to consult with the Privacy Policy Unit
Disincentives to seeking privacy advice were:
- the policy requirements for completing a privacy impact assessment are complex and demand a lot of time and resources, which, according to key informants, can create tension between engaging in a lengthy privacy impact assessment process and delivering a project on time
- the lack of capacity as completing a privacy impact assessment requires specific expertise that may be contracted to an external party or that may take considerable time to build internally
Interviewees stated that the privacy impact assessment process is outdated and does not support agile initiatives. Interviewees also stated that the Privacy Act and Directive on Privacy Practices are burdensome and do not allow for agile initiatives. Agile initiatives require nimble administrative processes so that pilots (which are riskier delivery models by nature) and proofs of concept can be delivered effectively and efficiently. While the legislation is out of scope for this evaluation, the legislation does:
- affect the ability of the Privacy Policy Unit to achieve its outcomes
- present a risk to achieving effective privacy practices
5.3 Resources
Expected outcome: The department has appropriate resources and succession planning to manage current and evolving privacy activities.
Conclusion: The resources to effectively manage privacy risks and the requirements of the department are inadequate, particularly in light of the new initiatives and lines of business that TBS is undertaking, as well as the new or changing skills required to support the evolution of privacy risks at TBS.
5.3.1 Why is this important?
The lack of appropriate resources could delay responses and decrease the value of advice to employees who are completing privacy impact assessments or who are managing privacy breaches. Privacy risks resulting from new lines of business may not be identified.
There is a risk that the privacy function at TBS may not be prepared to respond to growing and changing operational requirements. This may result in decreased service levels, increased privacy breaches and reputational damage.
5.3.2 Recommendation
The Privacy Policy Unit should supplement the business case with a formal human resources plan to identify the resources, competencies and skills needed to support the current volume of work and requirements for the future.
5.3.3 Findings
Level of effort spent on activities
The current workload of the Privacy Policy Unit requires a significant amount of overtime, which is not operationally sustainable (increases retention risk and potential for burnout). The workload has consistently increased over the past three years and is expected to continue increasing because of the changing and growing mandate of TBS, which includes, for example, digital government transformation.
The analysis suggests that resource management challenges are a constraint for the proactive management of privacy risk. These challenges hamper the focus of the Privacy Policy Unit on its role as a steward of sound privacy management, which includes:
- developing and implementing tools and awareness initiatives
- strengthening internal capabilities and skills to effectively support sectors
Resources and succession planning
Research on best practices based on generally accepted privacy principles states that entities should be provided with resources to implement and support their privacy policies.
The Privacy Policy Unit has developed a business case for additional resources, which is currently under deliberation. Resource gaps and the succession plan for the director position at the Privacy Policy Unit have been identified in the sector’s integrated business plan document. However, the document did not identify the skills needed to support the new initiatives and lines of business being undertaken by TBS.
Evidence from interviews suggested that there are three considerations for the near future:
- There is a risk that the skills found in the Privacy Policy Unit will be insufficient to effectively deliver advisory services for new initiatives or lines of business that are distinct from traditional TBS programs. One example of a new initiative is the Office of the Chief Information Officer’s support for the Treasury Board President’s mandate to make government data available digitally.Footnote 11 This initiative took on greater visibility when the Treasury Board President became Canada’s first minister of digital government in 2018. In light of the new focus on digital government, increased proactive risk management for these initiatives may be prudent.
Training on the technology used in TBS’s new lines of business could help the Privacy Policy Unit better understand the:
- work conducted by sectors
- project environments in areas such as cloud computing and artificial intelligence
Better understanding could result in more effective advice, guidelines and tools that reflect the changing needs of the sectors.
- Additional focus by the Privacy Policy Unit on developing tools for completing privacy impact assessments could result in cost efficiencies because there would be less reliance on external consultants.
6. Overall conclusion
Some areas of TBS collect and retain more personal information than others. These areas consult the Privacy Policy Unit more regularly and require ongoing engagement that is tailored to their specific business requirements. Efforts to improve the understanding and awareness of sectors and branches should be commensurate to their level of engagement with privacy issues.
The Privacy Policy Unit undertakes its activities according to the Privacy Act and the accompanying directive and guidelines. However, the length and complexity of the privacy impact assessment process is viewed as a barrier, especially for programs delivering enterprise-wide and agile initiatives. The Privacy Policy Unit does not have the mandate to change the legislation and the requirements for privacy impact assessments, but it can change how it undertakes assessments. Doing so could greatly reduce the time needed to complete a privacy impact assessment.
During the period examined, TBS did not experience a significant privacy breach (that is, one that must be reported under the Privacy Act). Until monitoring of privacy risk is formalized as an activity under the privacy program, there is no way to objectively assess whether privacy risks are adequately considered or reported in the department. Ultimately, this affects management’s ability to make informed decisions about privacy risk.
There is a high degree of satisfaction with the services offered by the Privacy Policy Unit. The Privacy Policy Unit is often sought out by the Office of the Chief Information Officer’s Information and Privacy Policy Division and other departments and agencies for expert advice in designing and delivering privacy services in the federal government. Moving forward, there is concern that the Privacy Policy Unit will not have the resources, competencies and skills required to adequately manage privacy risks and requirements for the department. This concern is particularly relevant now that agile initiatives and new technologies, such as cloud computing and artificial intelligence, are being added to the TBS repertoire of programs and, in some cases, are being implemented throughout government.
Canadians expect the government to protect their personal information by respecting the spirit and the requirements of the Privacy Act. By addressing the recommendations identified in this report, TBS will be better able to ensure that the personal information of Canadians is protected.
Appendix A: management response and action plan
Joint evaluation and audit of privacy practices
The Access to Information and Privacy (ATIP) Office, Strategic Communications and Ministerial Affairs (SCMA), has reviewed the joint evaluation and audit report and agrees with the recommendations. Proposed actions to address the recommendations of the report are outlined below.
Note: SCMA’s ATIP Office recently hired a dedicated senior ATIP advisor whose primary focus will be to further advance the implementation and ongoing activities of the action plan, including addressing the audit and evaluation recommendations outlined below.
Recommendation 1a
Develop a formal outreach and engagement plan and include mechanisms to monitor its effectiveness. (5.1.2)
Management response
Management agrees with the recommendation.
SCMA’s ATIP Office will develop a comprehensive privacy awareness strategy and outreach plan that identifies specific training requirements for TBS in an effort to ensure that all employees have a baseline understanding of their roles and responsibilities in the area of privacy.
Monitoring
This recommendation will be monitored by both evaluation and audit.
| Management action | Start date | Target completion date | Office of primary interest |
|---|---|---|---|
|
SCMA’s ATIP Office Resource: senior ATIP advisor |
Recommendation 1b
Expand its promotional efforts to ensure that:
- privacy requirements are communicated to those sectors that are not regularly involved in privacy initiatives
- training continues to be offered to sectors with more in-depth or specialized needs. (5.1.2)
Management response
Management agrees with the recommendation.
SCMA’s ATIP Office will supplement existing guidance materials to promote the core privacy requirements in an effort to:
- ensure that all TBS employees have a baseline understanding of their roles and responsibilities with regard to the protection of privacy
- further build a culture of compliance with the Privacy Act
Monitoring
This recommendation will be monitored by both evaluation and audit.
| Management action | Start date | Target completion date | Office of primary interest |
|---|---|---|---|
The following actions were pursued and completed while the audit and evaluation were ongoing:
|
SCMA’s ATIP Office Resource: senior ATIP advisor | ||
In response to the audit and evaluation recommendations, the following actions will be undertaken:
|
SCMA’s ATIP Office Resource: senior ATIP advisor |
Recommendation 2
The Privacy Policy Unit should re-examine the design and implementation of its privacy impact assessment procedures in consultation with the Office of the Chief Information Officer’s Information and Privacy Policy Division. (5.2.2)
Management response
Management agrees in part with the recommendation.
SCMA’s ATIP Office will continue to examine its existing tools and resources to:
- identify areas to streamline the privacy impact assessment process at TBS
- develop new materials to better support program officials in meeting existing Privacy Act requirements
However, SCMA’s ATIP Office remains limited in its ability to make significant modifications to the overall privacy impact assessment process in light of the current legislative and policy landscape, which applies to all government institutions.
Monitoring
This recommendation will be monitored by both evaluation and audit.
| Management action | Start date | Target completion date | Office of primary interest |
|---|---|---|---|
|
SCMA’s ATIP Office Resource: senior ATIP advisor |
Recommendation 3
Privacy Policy Unit should supplement the business case with a formal human resources plan to identify the resources, competencies and skills needed to support the current volume of work and the requirements for the future. (5.3.2)
Management response
Management agrees with the recommendation.
SCMA’s ATIP Office has already begun to address resourcing issues by committing financial resources to staff additional positions in the Privacy Policy Unit and is currently conducting staffing processes to fill those positions. A formal human resources plan is forthcoming to supplement the existing business case.
Monitoring
This recommendation will be monitored by audit.
| Management action | Start date | Target completion date | Office of primary interest |
|---|---|---|---|
|
SCMA’s ATIP Office Resource: senior ATIP advisor |
Appendix B: definitions
A privacy impact assessment is a process that helps departments and agencies determine whether new technologies, information systems and initiatives, or proposed programs and policies meet basic privacy requirements.
A privacy breach is the improper or unauthorized collection, use, disclosure, retention or disposal of personal information. When a breach is reported to the Privacy Policy Unit, a process is undertaken to assess the breach, contain it, notify the personsaffected and mitigate the breach.
A privacy notice statement is expert advice from the Privacy Policy Unit that interprets applicable sections of the Privacy Act to inform individuals about how their information will be collected and managed.
A document review is a review by the Privacy Policy Unit of a program area’s documentation for privacy considerations.
An internal consultation is a meeting between the Privacy Policy Unit and an area in TBS so that the unit can deliver advice about the interpretation of the Privacy Act and the accompanying directives and guidance.
A training session provides information about the Privacy Act and the accompanying directives and guidance to an area in TBS based on the area’s specific needs.
Appendix C: evaluation questions, audit criteria, conclusions and the Treasury Board of Canada Secretariat Access to Information and Privacy Office’s logic model
The figure below shows:
- the evaluation questions and conclusions and the audit criteria and conclusions
- which components and elements of the Treasury Board of Canada Secretariat (TBS) Access to Information and Privacy Office’s logic model were addressed in the evaluation and in the audit
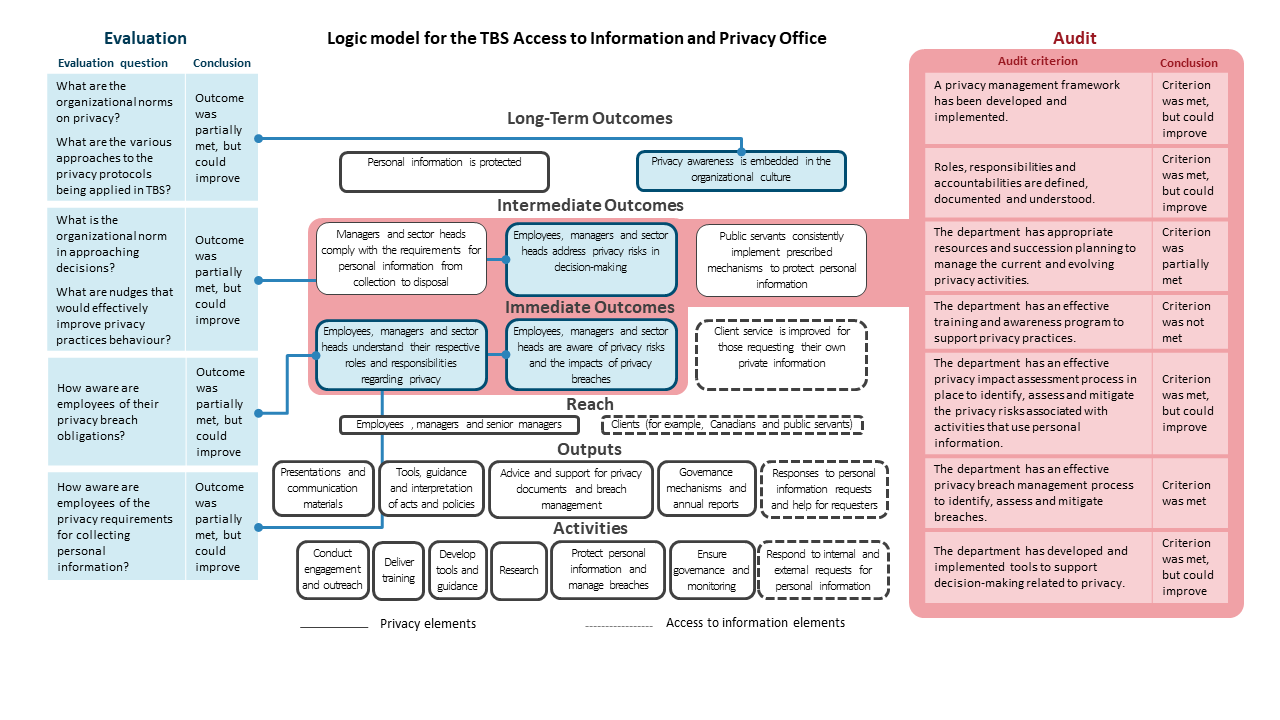
Figure 4 - Text version
The figure in Appendix C is composed of:
- the evaluation questions and conclusions, which are shown on the left-hand side of the figure
- the audit criteria and conclusions, which are shown on the right-hand side of the figure
- the logic model for the TBS Access to Information and Privacy Office, which is in the centre of the figure
The logic model shows:
- which elements are privacy elements and which elements are access to information elements
- which outcomes and elements were covered by the evaluation and which outcomes and elements were covered by the audit
| Evaluation question | Outcome and element of the logic model covered | Conclusion |
|---|---|---|
| What are the organizational norms on privacy? | Long-term outcome: Privacy awareness is embedded in the organizational culture | Outcome was partially met, but could improve |
| What are the various approaches to the privacy protocols being applied in TBS | Long-term outcome: Privacy awareness is embedded in the organizational culture |
Outcome was partially met, but could improve |
| What is the organizational norm in approaching decisions? | Intermediate outcome: Employees, managers and sector heads address privacy risks in decision-making | Outcome was partially met, but could improve |
| What are nudges that would effectively improve privacy practices behaviour? | Intermediate outcome: Employees, managers and sector heads address privacy risks in decision-making |
Outcome was partially met, but could improve |
| How aware are employees of their privacy breach obligations? | Immediate outcomes:
|
Outcome was partially met, but could improve |
| How aware are employees of the privacy requirements for collecting personal information? | Immediate outcomes:
|
Outcome was partially met, but could improve |
The audit covered the following outcomes and elements of the logic model:
- Intermediate outcome: managers and sector heads comply with the requirements for personal information from collection to disposal
- Intermediate outcome: Employees, managers and sector heads address privacy risks in decision-making
- Intermediate outcome: Public servants consistently implement prescribed mechanisms to protect personal information
- Immediate outcome: Employees, managers and sector heads understand their respective roles and responsibilities regarding privacy
- Immediate outcome: Employees, managers and sector heads are aware of privacy risks and the impacts of privacy breaches
| Audit criterion | Conclusion |
|---|---|
| A privacy management framework has been developed and implemented. | Criterion was met, but could improve |
| Roles, responsibilities and accountabilities are defined, documented and understood. | Criterion was met, but could improve |
| The department has appropriate resources and succession planning to manage the current and evolving privacy activities. | Criterion was partially met |
| The department has an effective training and awareness program to support privacy practices. | Criterion was not met |
| The department has an effective privacy impact assessment process in place to identify, assess and mitigate the privacy risks associated with activities that use personal information. | Criterion was met, but could improve |
| The department has an effective privacy breach management process to identify, assess and mitigate breaches. | Criterion was met |
| The department has developed and implemented tools to support decision-making related to privacy. | Criterion was met, but could improve |
The logic model is in the centre of the figure. The main components of the logic model, from the bottom to the top, are:
- Activities
- Outputs
- Reach
- Immediate outcomes
- Intermediate outcomes
- Long-term outcomes
Each component is composed of various elements. There are 2 types of elements: privacy elements and access to information elements.
The Activities component is composed of the following privacy elements:
- Conduct engagement and outreach
- Deliver training
- Develop tools and guidance
- Research
- Protect personal information and manage breaches
- Ensure governance and monitoring
The Activities component is composed of the following access to information element:
- Respond to internal and external requests for personal information
The Outputs component is composed of the following privacy elements:
- Presentations and communication materials
- Tools, guidance and interpretation of acts and policies
- Advice and support for privacy documents and breach management
- Governance mechanisms and annual reports
The Outputs component is composed of the following access to information element:
- Responses to personal information requests and help for requesters
The Reach component is composed of the following privacy element:
- Employees, managers and senior managers
The Reach component is composed of the following access to Information element:
- Clients (for example, Canadians and public servants)
The Immediate Outcomes component is composed of the following privacy elements:
- Employees, managers and sector heads understand their respective roles and responsibilities regarding privacy
- Employees, managers and sector heads are aware of privacy risks and the impacts of privacy breaches
The Immediate Outcomes component is composed of the following access to Information element:
- Client service is improved for those requesting their own private information
The Intermediate Outcomes component is composed of the following
privacy elements:
- Managers and sector heads comply with the requirements for personal information from collection to disposal
- Employees, managers and sector heads address privacy risks in decision-making
- Public servants consistently implement prescribed mechanisms to protect personal information
The Long-Term Outcomes component is composed of the following privacy elements:
- Personal information is protected
- Privacy awareness is embedded in the organizational culture