Audit of the Governance Framework over Information Management
3.0 Detailed Observations and Recommendations
IM Governance Structure at CIC
IAAB expected to find governance structures, mechanisms and resources in place to ensure the continuous and effective management of information.
A Knowledge and Information Management Committee (KIMC) has been established and has a terms of reference. The KIMC is a director-level committee responsible for developing courses of action and recommendations for addressing CIC’s IM concerns. KIMC meetings are expected to be held monthly or as needed. The following figure depicts the reporting relationship between KIMC and key CIC committees:
Figure 2: IM Governance Committees and Escalation/Approval Mechanism
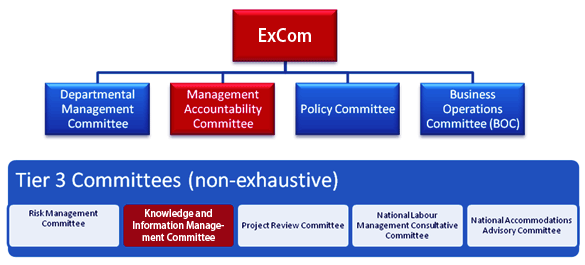
Figure 2 presents the different levels of governance committees involved in information management at CIC. At the base of the diagram is a non-exhaustive list of Tier 3 committees including: the Risk Management Committee, the Knowledge and Information Management Committee, the Project Review Committee, the National Labour Management Consultative Committee and the National Accommodations Advisory Committee. The next level of governance committees includes: the Departmental Management Committee, the Management Accountability Committee, the Policy Committee and the Business Operations Committee. Finally, the most senior governance committee at CIC is the Executive Committee (ExCom). The diagram also demonstrates that the escalation and approvals mechanism at CIC for issue escalation or approvals moves upward from the Knowledge and Information Management to the Management Accountability Committee and finally, to the Executive Committed, if required.
Escalation and approvals required from KIMC meetings are scheduled for CIC’s Management Accountability Committee (MAC), a director-general level steering committee with a strategic focus on strengthening accountability in the Department. The MAC assesses the need to forward IM instruments to the Executive Committee (ExCom) for approval. ExCom is the senior decision-making forum for CIC and focuses on issues that require decision making and strategic direction, and on corporate and horizontal issues.
Delegated responsibility for participating in interdepartmental governance committees rests primarily with the CIO. The CIO sits on the Management Accountability Committee, the Departmental Management Committee and the Client Services Committee. Membership in these committees enables the CIO to inform and educate the Department about IM, to raise IM-related concerns for discussion and approval, and to seek input on and approval of various IM engagements. It also ensures that the CIO is informed of key departmental IM initiatives. During his weekly senior management team meetings, the CIO shares information with the directors who report to him, and those directors share information horizontally with each other and with key representatives from the GCMS and Biometrics projects.
The CIO is also a key member of several director-level IM-related working groups that bring together people from various IMTB groups and CIC initiatives to ensure the successful development and implementation of data policies, procedures and guidelines. These working groups include the Data Steering Working Group, the Biometrics Inter-Project Working Group, the Enterprise IM/IT Architecture and Standards Committee, and a related director-general level data production working group.
Meeting CIC’s Strategic and Business Objectives
IAAB expected to find that CIC’s IM program and plans meet the needs of CIC’s strategic and business objectives, programs and services.
The IM Strategic Plan 2010-2013, developed by the KIMC and approved by the MAC, identifies how the Department will meet its IM obligations under the relevant legislation and TBS policy. The Strategic Plan details IM initiatives and divides them into the following four high-level themes: foster a collaborative work environment; achieve IM convergence; strengthen physical and electronic record keeping; and enhance knowledge channels.
The IM Strategic Plan includes many key components, such as goals and objectives, strategic drivers, initiatives, milestones, and a communication plan. The Strategic Plan would be strengthened if it included CIC IM directives, risk mitigation strategies, a human resources plan for IM and an IM performance measurement strategy with key performance metrics or indicators. The Plan includes reference to the Management Accountability Framework and to the Information Management Capacity Check Tool, in addition to outlining four high level themes; however, it is unclear how these items will be prioritized or measured to evaluate IM performance.
An IMD Strategic Plan Milestone Summary Spreadsheet exists, but it could be improved to more effectively measure the progress of the IM Strategic Plan and associated initiatives. Currently, the spreadsheet identifies only the quarter in which milestones or initiatives are expected to be completed and therefore overlooks two key elements: first, who is accountable for the success of each IM initiative; second, an assessment of the variance between planned and actual resources, particularly as they relate to timelines, human resources, and high-level cost estimates for each initiative.
As a result, the IMD’s progress on IM strategic goals and initiatives remains uncertain.
Consultation
The development of an IM strategic plan requires input from key stakeholders from across the Department. An in-depth review of KIMC meeting minutes and records of decision provided no evidence that senior management stakeholders from relevant branches (IM users) or decision-making committees (the MAC and ExCom) were consulted during the development of CIC’s draft IM Strategic Plan. Also, the IM Director dedicates only a portion of his time to IM-focused activities; the remainder of his time is dedicated to IT and related administration.
Knowledge and Information Management Committee (KIMC)
KIMC meeting minutes from March 2010 to July 2010 contain evidence of high-level discussions on strategies, tools and instruments needed to address overall IM scope, importance and vision. Despite the IM governance responsibilities of the MAC and ExCom, however, the KIMC meeting minutes provided no indication that IM issues are escalated to either committee for further discussion. Interviews confirmed that IM is rarely included as a formal ExCom agenda item, and, although ExCom wants to review the IM Strategic Plan, the Plan is not yet ready to be presented.
When IM objectives, roles and responsibilities are not clearly understood at the executive level, management cannot help the IMTB achieve CIC-wide IM objectives and maintain key controls.
Conclusion
Overall, the governance structure, mechanisms, and resources are in place at CIC to support the management of information throughout its lifecycle. The IM Strategic Plan 2010-2013 has been approved by the MAC and includes key IM elements (for example, goals and objectives, and strategic drivers); however, it could be improved by adding components that would more effectively define CIC’s strategic direction for IM. Also, consultations and input from key stakeholders could be incorporated into the decision-making process.
Recommendation 1
IMTB should enhance the current IM Strategic Plan by developing IM standards, an IM performance measurement strategy and an IM human resource plan.
Management Response
The Director General, Chief Information Officer (CIO) and Information Management Senior Officer (IMSO) of IMTB agrees with the recommendation.
In consultation with TBS (functional owner of IM) and LAC (functional authority for record keeping), IMD will develop or update IM standards by March 31, 2012.
In consultation with CIC stakeholders (all sectors and regions), IMD will update the IM Strategic Plan that will include an IM performance measurement strategy and IM human resources plans. Approvals will be obtained from the Knowledge and Information Management Committee, MAC and ExCom before October 31, 2011.
Recommendation 2
IMTB should ensure that the IM Strategic Plan is presented to ExCom for their review and approval. This would generate organization-wide visibility and would serve as a mechanism to enlist the support of senior managers in communicating and promoting IM-aware behaviours.
Management Response
The IMSO agrees with the recommendation. IMD will present the updated IM Strategic Plan to ExCom for approval before October 31, 2011.
IAAB expected to find that IM risks are identified and documented along with the risk responses and mitigation strategies.
IM Strategic Plan
The IM Strategic Plan is the most appropriate vehicle for documenting IM risks and risk mitigation strategies. The Plan includes a risk assessment, but that assessment does not include details on specific strategies for minimizing the impact and significance of the identified risks.
Limited information on IM risks means that senior management does not have the necessary information when making decisions about shifting priorities and allocating resources. In addition, the IM Strategic Plan provides little guidance to the IM steering committee on how to manage IM risks at an operational level.
IM/IT Project Prioritization
Because new IM/IT projects could introduce IM risks not envisioned in the IM Strategic Plan, IAAB expected to find that IM/IT projects are reviewed for IM implications.
A department-wide IM/IT project prioritization process occurs every year and involves key stakeholders at senior management levels. Once projects have been selected, CIC project charters related to IM/IT do not require review by the IM which is contrary to best practices in leading IM organizations. A review of project charters by the IMD would ensure integration with existing systems and consistency with the Department’s long-term IM strategy. This would ensure that IM investments are used to their full potential and that risks are addressed.
Conclusion
IM risk management is a component of CIC’s overall approach to risk management. The ubiquitous nature of IM and the integrated nature of risk management mean that other approaches to risk management at CIC (for example, the corporate risk profile with quarterly monitoring) help mitigate the IM risks noted in this audit. However, further strengthening risk management in the area of IM will, in turn, help strengthen CIC’s risk management efforts.
Recommendation 3
IMTB should enhance the current IM Strategic Plan by developing a detailed risk mitigation plan
Management Response
The IMSO agrees with the recommendation.
In consultation with CIC stakeholders (all sectors and regions), IMD will update the IM Strategic Plan to include a detailed risk mitigation plan. Approval will be obtained from the Knowledge and Information Management Committee, MAC and finally from ExCom before October 31, 2011.
Recommendation 4
IMTB should ensure that the Project Charter approval process for all IM/IT initiatives includes sign off from the Director, Information Management.
Management Response
The IMSO agrees with the recommendation.
IMD will submit this recommendation to the IMTB Management Committee for approval before September 30, 2011.
IAAB expected to find management and operational controls in place to ensure the continuous and effective management of information.
IM supporting tools and systems
The main tool used to support the management of documents and information at CIC is the Records, Document and Information Management System (RDIMS). The Department has a number of stand-alone finance and operational systems that store their own data, but RDIMS is intended to be the repository for records generated by staff based on the output from those other systems. Although RDIMS has been rolled out to 80% of the Department, it is not a mandatory tool and is not universally used. During the interviews conducted as part of this audit, a number of reasons were identified for this lack of uptake:
- Lack of training
- Problems with version control and determining whether the most current version of a document is in RDIMS;
- Lack of familiarity with naming conventions makes it difficult to locate documents; and
- Dissatisfaction with RDIMS search capability.
As a result of the lack of RDIMS use, information is also stored on shared network drives throughout the Department and on stand-alone software applications.
Without organization-wide RDIMS adoption and use, CIC cannot reap the benefits of this corporate technology-based IM system, which is designed to be used to manage document access, version control, ATIP requests, and information disposition. Developing and supporting stand-alone systems increases the cost and the risks associated with IM in the Department.
Secret Documents
Managing documents classified “Secret” and above is a challenge faced by all government departments, as the cost of securing the computer network that stores such information can be prohibitive. At CIC, these documents are managed in hard-copy format and are stored in locked cabinets across the Department. No central tracking is done.
This approach has two disadvantages. First, rotational positions are common at CIC and it is difficult for staff in these positions to know exactly what documents are locked in their cabinets when they begin a new posting. Second, the inability to track secret documents makes version control difficult since several copies of a document may exist.
The lack of a systematic process for tracking and locating secret documents means that the organization does not know what classified documents are distributed across the organization, who is accountable for them and who has access to them.
Delegated roles, responsibilities, and accountability structure
The senior official responsible for IM (the IMSO) at CIC is the CIO, who is the DG, Information and Technologies. As part of his responsibilities, the IMSO has delegated authority and sits on a number of departmental committees
The Director of IM, who is responsible for both IM and IT duties, heads the IMD.
The Director of IM also chairs the KIMC. This director-level committee is responsible for developing courses of action and recommendations for addressing CIC’s IM concerns. KIMC meetings are expected to be held monthly or as needed. Established roles, responsibilities, and accountabilities ensure that IM issues are managed in accordance with delegated authorities.
Two areas relate closely to IM but fall outside the responsibilities of the IMSO: Access to Information and Privacy, and management of memorandums of understanding (MOUs) with external stakeholders. While accountability for these areas falls outside the scope of this audit, the extent to which both areas are able to access the information they need to meet their objectives was included in the audit scope and is reflected in the observations and recommendations.
Retention and Disposition
Interviews indicated that retention and disposition strategies vary across CIC. The IMD plans to establish record-disposition authorities for each information system, but work has not yet begun. IMD is behind schedule on developing retention and disposition schedules, with only 8 of the 17 required schedules formalized.
A retention and disposition strategy is vital to the organization, as it allows for a clear understanding of requirements and responsibilities. Without clear guidance, users may keep records longer than required, and thereby increase costs; or, conversely, they may destroy records that should be kept.
Information Sharing
CIC shares information with many partners. Work is under way to centralize the management of the MOUs that govern this sharing of information. Although it is beyond the scope of this audit, it remains uncertain how CIC’s MOU partners will comply with and reflect CIC’s IM policies and procedures when using CIC information.
Conclusion
Although control elements are in place and roles and responsibilities are clearly defined, the management control framework for IM could be improved in certain areas. A continued focus on adoption of RDIMS in lieu of branch-specific IM tools, the management of secret and classified information, and the establishment of record-disposition authorities will strengthen the overall control framework and mitigate IM and operational risks.
Recommendation 5
IMTB should investigate the root causes of the lack of RDIMS adoption in order to develop and implement a remediation plan.
Management Response
The IMSO agreed with the recommendation at the time of the audit.
However, the RDIMS software that presently exists at CIC is approaching the end of its life and therefore IMTB is now focused on implementing a newer, robust solution called GC Docs (ECM LiveLink 10). The movement to this newer solution is in accordance with the Government of Canada’s new direction to deliver Document and Records Management (DRM) functionality as a Software, as a Service (SaaS) for federal departments that is consistent with the GC IM Strategy, IM policy, directives and standards, and aligned to departmental requirements and the ITSS Community Cloud Security Framework. Consequently, IMTB will not be investing additional resources to inquire as to the root causes for the lack of adoption of the RDIMS tool. IMTB will instead invest time and resources into advancing the GC Docs (ECM LiveLink 10) solution at CIC.
IMD is partnering with TBS, LAC and best of breed GoC implementers of Electronic Record Document Management Software (EDRMS) to build IM business requirements to ensure that the GC Docs implementation addresses the root causes of the issues associated with RDIMS.
Recommendation 6
IMTB should investigate options for central storage and tracking of documents that are not stored in RDIMS because of their security classification.
Management Response
The IMSO agrees with the recommendation.
IMTB has begun investigating options for central storage and tracking of documents which are not stored in RDIMS because of their security classification. Full implementation will be finalised on March 31, 2014.
Recommendation 7
IMTB should ensure that the requirements of MOUs that govern information sharing align with CIC’s IM policies and procedures, and implement measures to ensure that information sharing partners adhere to CIC’s policies under those MOUs.
Management Response
The IMSO agrees with the recommendation.
The creation of the Information Sharing Branch as a central repository for all MOUs has enhanced CIC’s ability to follow through with verification that data sharing agreements will respect the CIC Business Process Mappings and Business Record Definitions. Functional authority for this repository is being transferred to International and Intergovernmental Relations Branch.
Making the MOUs accessible and findable will be completed before September 2011. The CIC Library’s public-facing catalogue houses the access points and the electronic storage is presently being studied. The implementation of an information-sharing control framework is a considerably larger and more complex initiative with multiple interdependencies within CIC. Insofar as there are in excess of 500 MOUs that will require the engagement of information-sharing partners, IMTB will need to ensure that it is adhering to the policy requirements that are pertinent to these agreements. To do so, this will require building capacity, as well as reconciling the large volume of MOUs with partners. This will be finalized on March 31, 2015.
Recommendation 8
IMTB should continue with the development of the disposition and retention schedules to ensure compliance with LAC requirements, as well as ensure that compliance with R&D schedules is tracked.
Management Response
The IMSO agrees with the recommendation.
IMTB completed the development of all CIC retention and disposition schedules on May 31, 2011. By March 31st , 2012, CIC will have identified and defined its records of business value. This is in accordance with the TBS Recordkeeping Directive (April 20, 2009). Thereafter, IMTB will begin identifying a compliance tracking methodology that can be used from an operational perspective.